
Update: January 04, 2018
Introduction
The purpose of this lab is to give the participant hands on experience of Security Monitoring and Analytics Cloud Service and how they can leverage this service to enable rapid detection and investigation of security threats.
This lab will be broken up into two parts. Part A will consisit of a simple walkthrough of a shared SMA environment which already has some log data uploaded. Part B is optional, will be more advanced and will be completed in your own SMA environment into which you will upload sample data and evaluate threats.
To log issues, click here to go to the github oracle repository issue submission form.
Objectives
In this lab, we will cover –
Part A
- Accessing the shared SMA environment
- Evaluating users with associated threats
- Understanding the value of the OMC unified platform
Part B
- How to access your SMA environment
- Enabling SMA service
- Reviewing pre-configured correlation rules
- Creating alert rules
- Uploading sample data
- How to evaluate threats
Pre-requisites
The following are minimum requirements for this lab
- Oracle Cloud Trial account with OMC instance provisioned. Refer to How to request your free trial account if you haven’t already done so. «««< HEAD
- Sample data: Staged on the linux host provided (Part B only)
- A computer with an internet connection and an SSH client (Part B only)
Part A
Accessing the shared SMA environment
- Click on the following link which will take you to the shared SMA environment
- https://clouddays-natdsecurity.itom.management.us2.oraclecloud.com/emsaasui/emcpdfui/welcome.html?DOMAIN-INSTANCE-NAME=clouddays
-
Sign in with the username and password provided by the session proctor
- This is the OMC landing page showing all the available services. Let’s click on “Security Monitoring and Analytics” to access the SMA Cloud Service
- SMA is a unified SIEM and UEBA cloud solution that helps to identify advanced threats and enables faster time to detection by leveraging machine learning techniques along with very high performance and scale by being built on a big data platform.
Evaluating users with associated threats
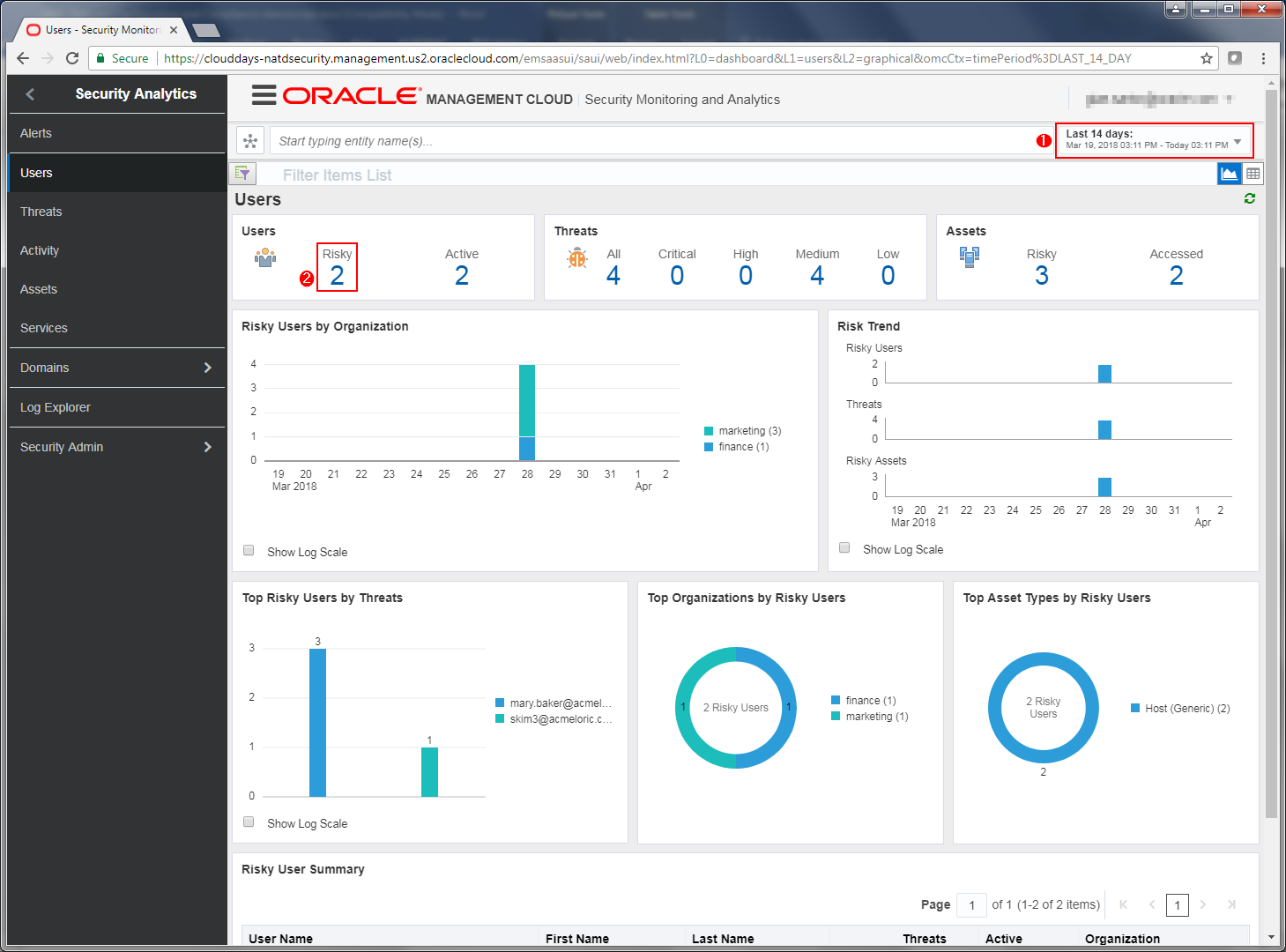
- You are now looking at the main SMA Landing page showing the “Users” Dashboard. Take a minute to review the different dashboards and corresponding data shown for the time period selected.
- Set the time period in the top right of the screen, selecting the time range of “Last 14 Days”
- Users – shows the total number of risky users
- Threats - shows total, critical, high, medium and low risk threats
- Assets – shows the total number of risky assets
-
In the Users area of the page, click the number below risky to drill fown in to Risky users
-
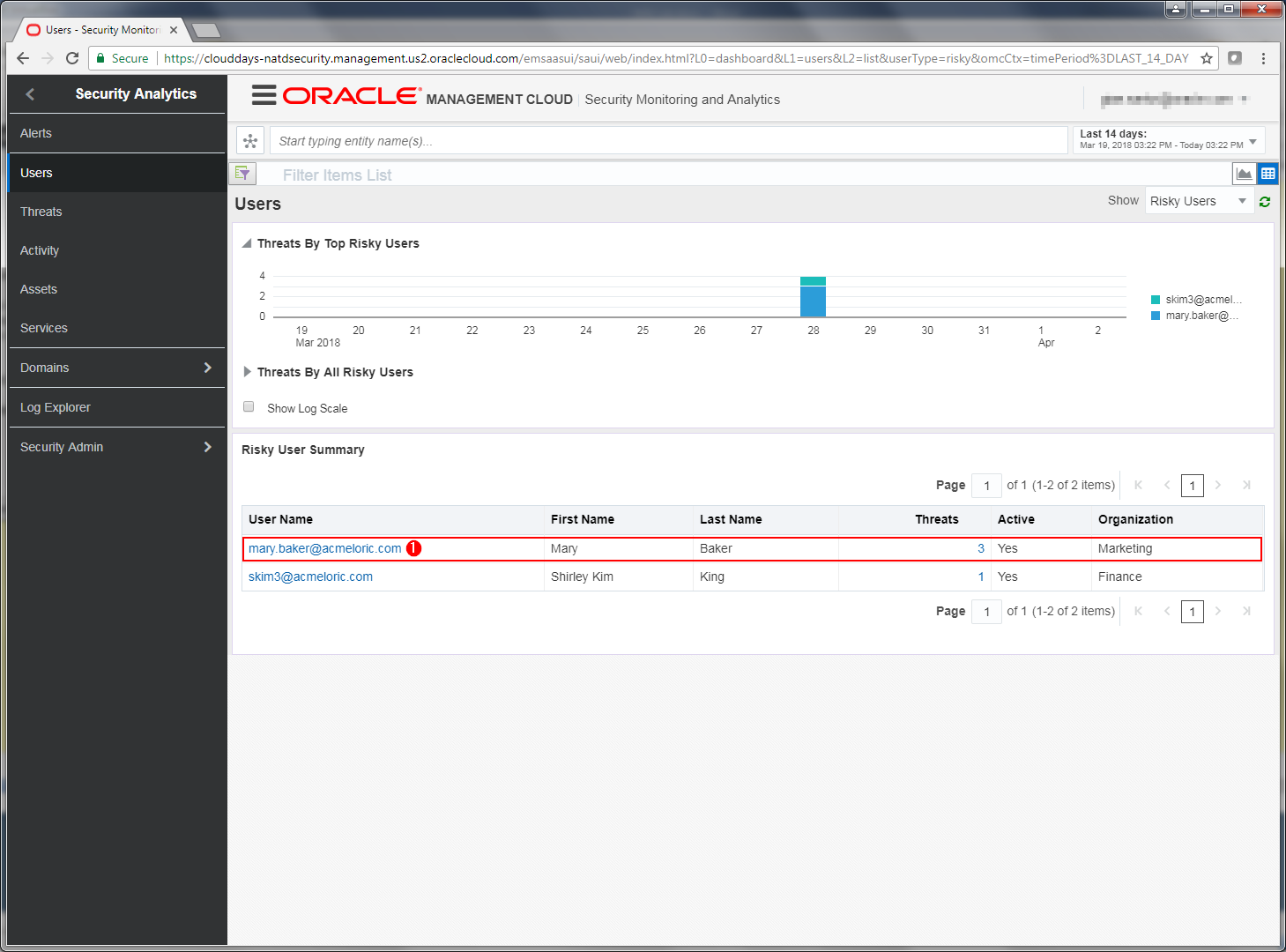
At the bottom of the page you can see a summary of risky users which is sorted with the most risky users at the top of the list. We can see that Mary Baker has the highest number of threats. Note that we can see Mary is a member of the Marketing department.
-
Click on mary.baker@acmeloric.com to investigate threats by Mary
- Here we can get more details on Mary. We see her organization, manager, whether she is active employee, her access is locked or not, phone number, email and location. Summary View shows:
- Threats by category
- Top Risky Assets by Threats
- Threats by Asset Type
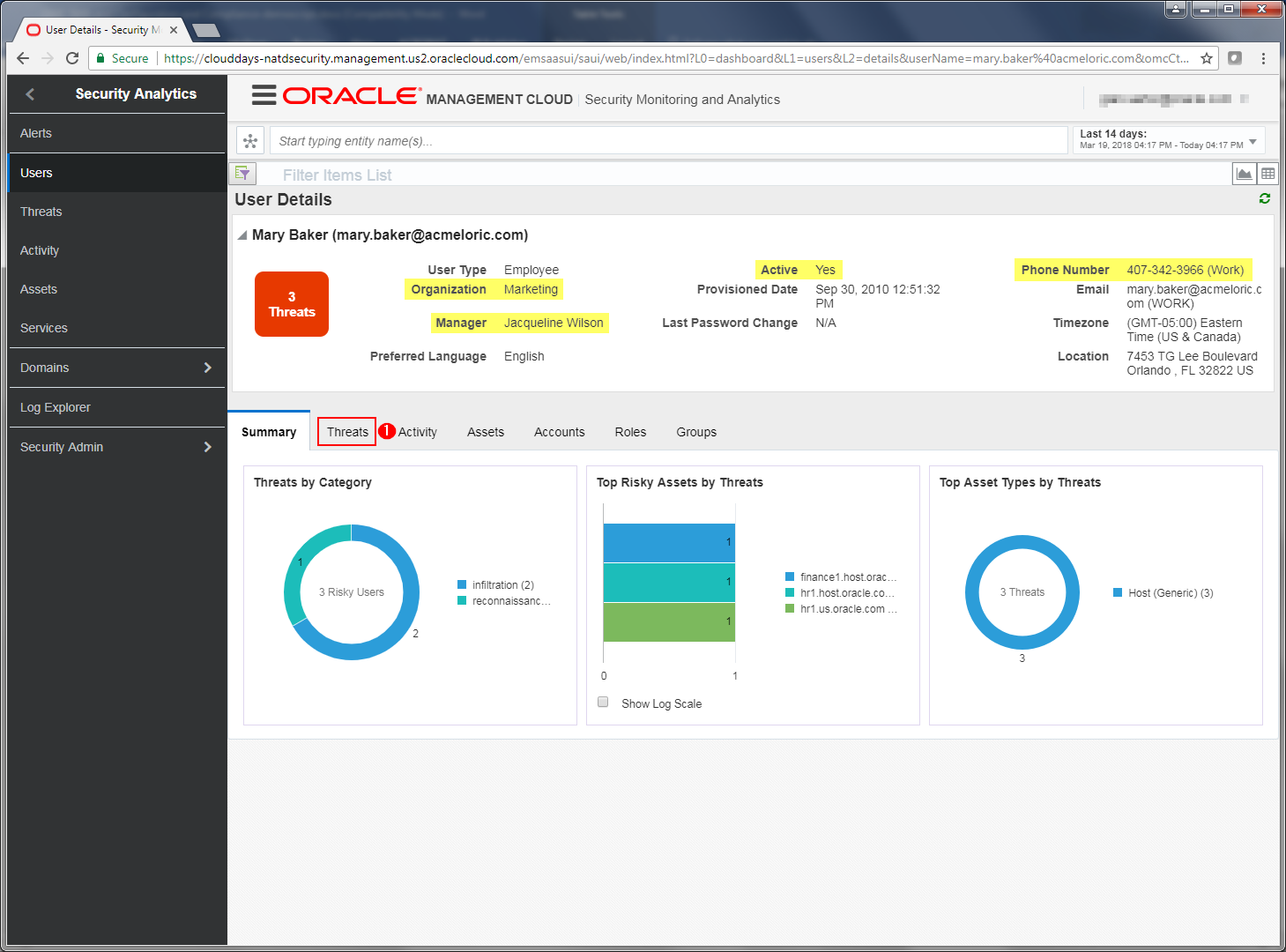
- Click on the Threats tab in the User details window.
- We are now looking at the Threat timeline and we can view this timeline by Risk Level or we can change the view and view the timeline by Threat category to view the events classified in the kill chain
-
In the Threat Details section near the bottom of the page, we can see the various threats associated with user Mary Baker. Two threats have been classified as “infiltration” type events and one has been classified as “reconnaissance”
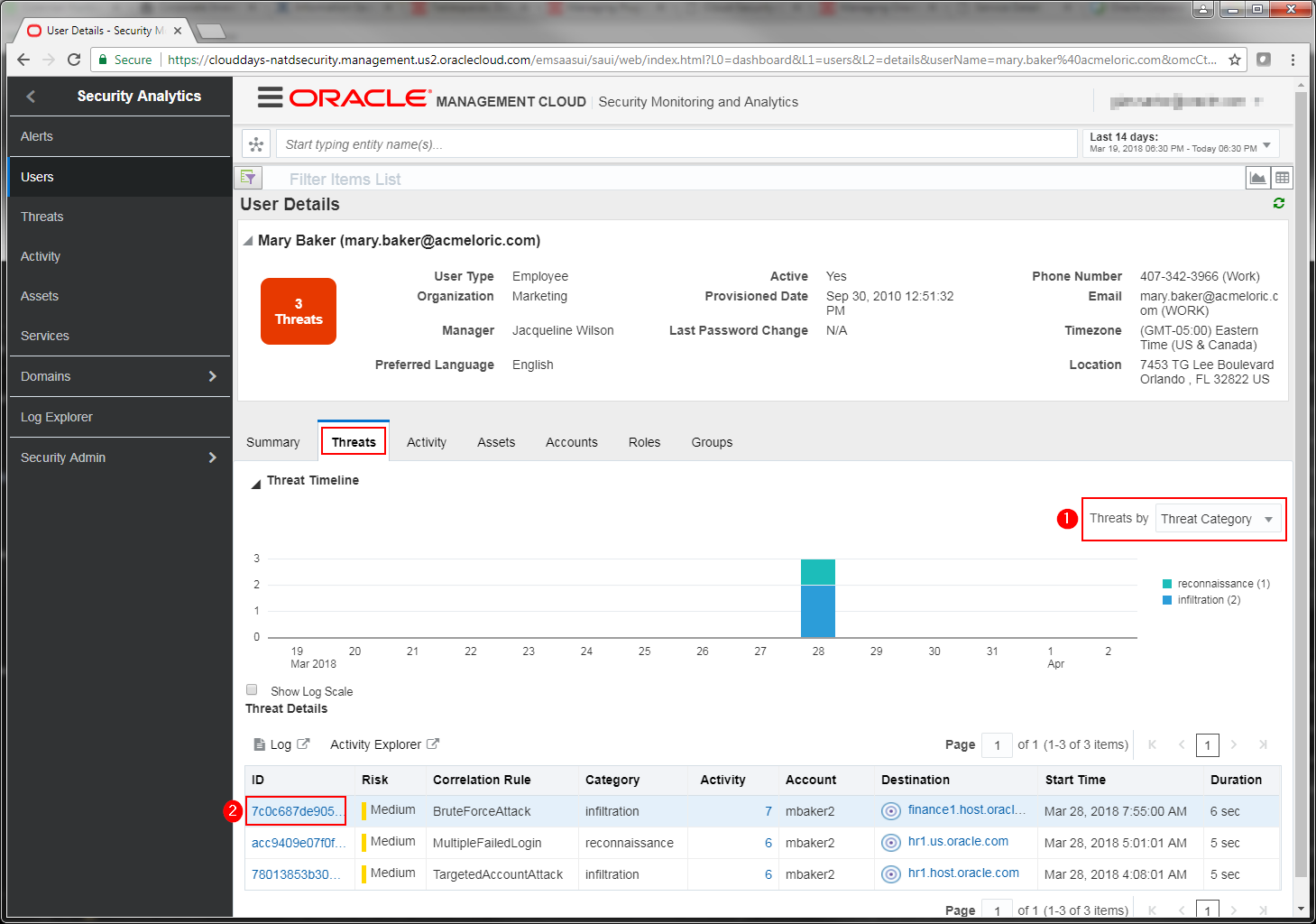
- Lets drill down and get some more information about the BruteForceAttack event. Click on the event id name in the ID column.
-
You are now looking at the expanded Threat Details pane which is giving you yet more details of the individual events comprising this threat.
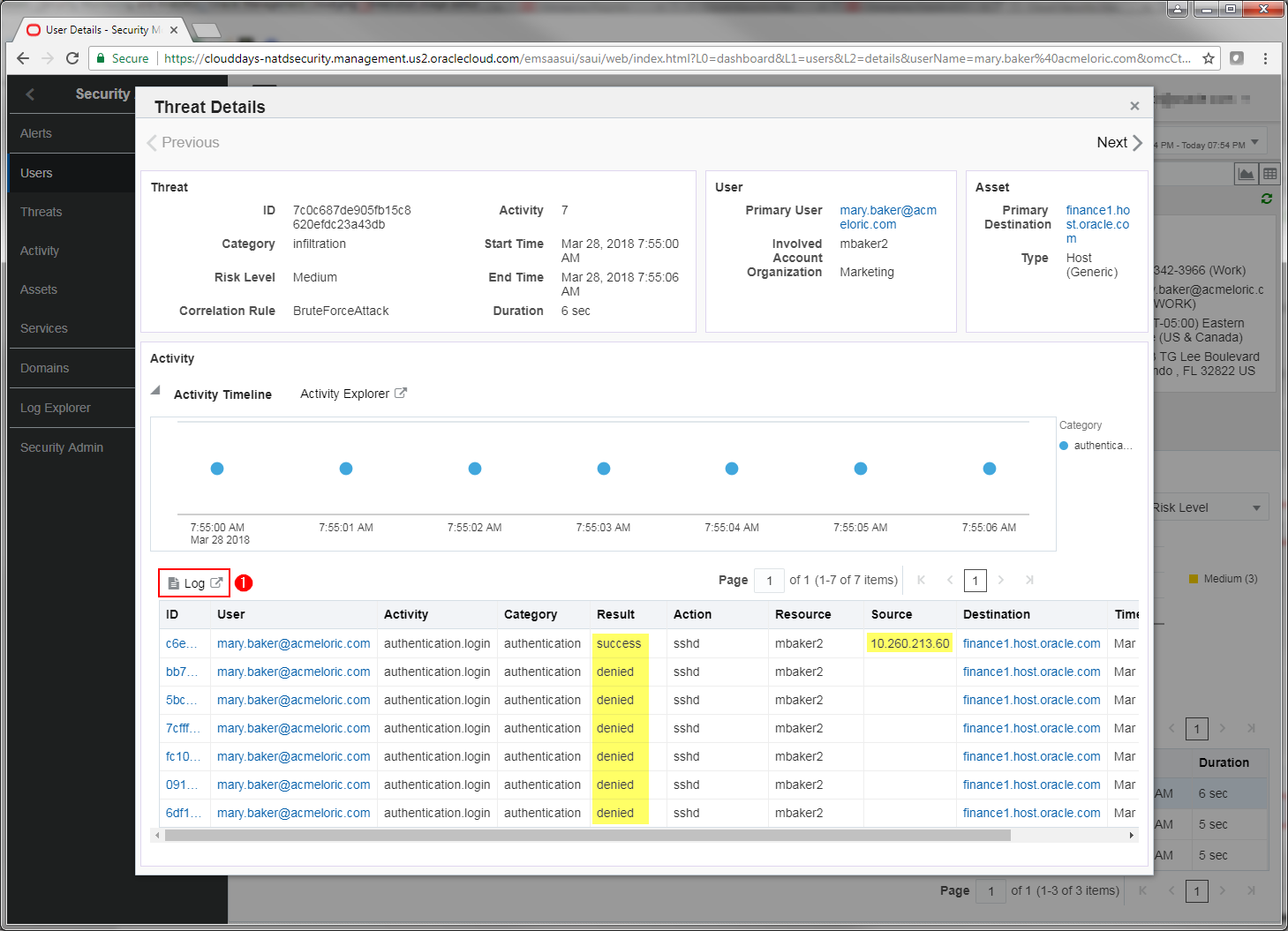
Understanding the value of the OMC unified platform
-
Click the Log link
-
Another tab is now open in your browser and we are looking at the individual log events in Log Analytics.
- This is great strength of our unified platform. Typically a security analyst may have to switch between multiple systems when investigating a security incident. Notifications may be sent by one system but log data may be contained in another system. Here we have easily switched to the log aggregator where we could perform yet further analysis on the events, searching for other types of related activity.
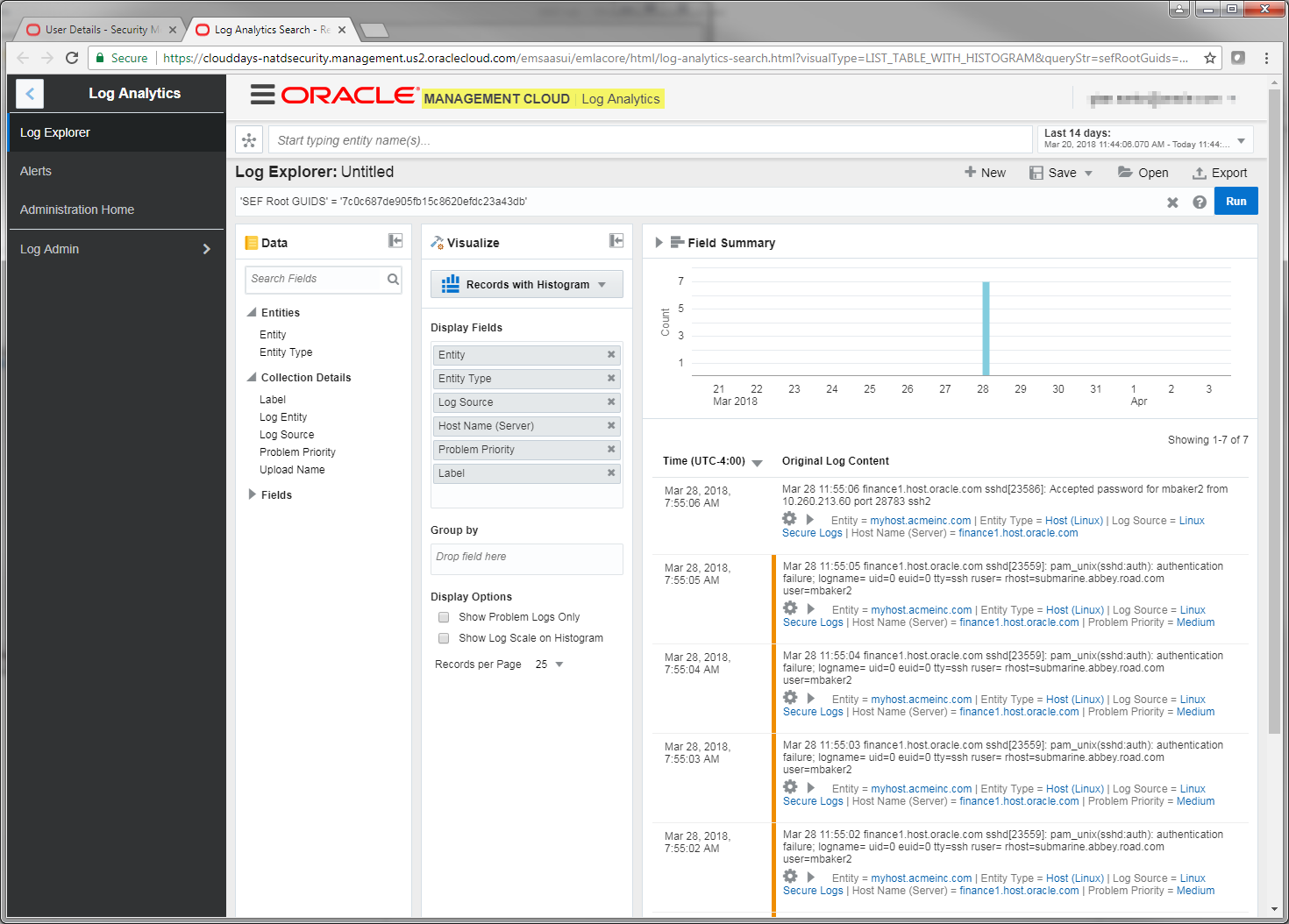
Part B
STEP 1 - Accessing your Environment & Initial Configuration
Accessing your OMC Instance
-
Navigate to one of the URLs in your Service Activation email to access the service. You will be prompted to change the password on first login.
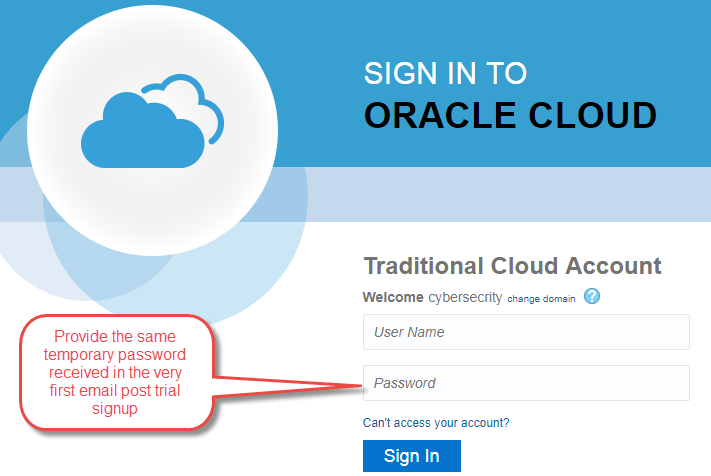
-
Create a new password and provide challenge Q&A for resetting should you ever need to.
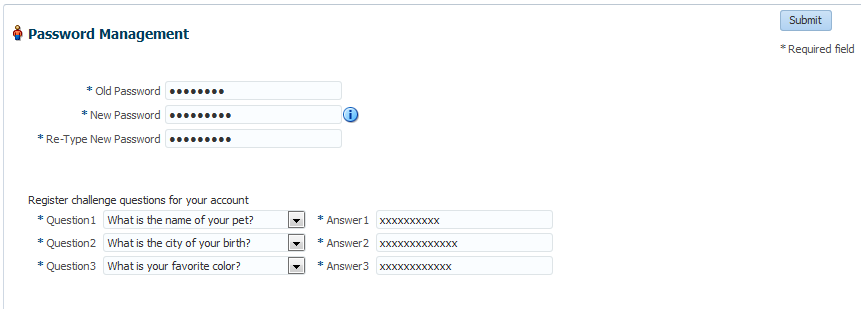
-
You’re are now ready to start using any of the services shown below. Our focus with be narrowed to “Security Monitoring and Analytics”
Instance Configuration
Prior to using the new service the following minimum configuration:
- Enable Security Monitoring & Analytics
- SMA alert rules
Enabling Security Monitoring Analytics
-
Navigate to
Menu Icon->Home->Administration->Entities Configuration->Licensing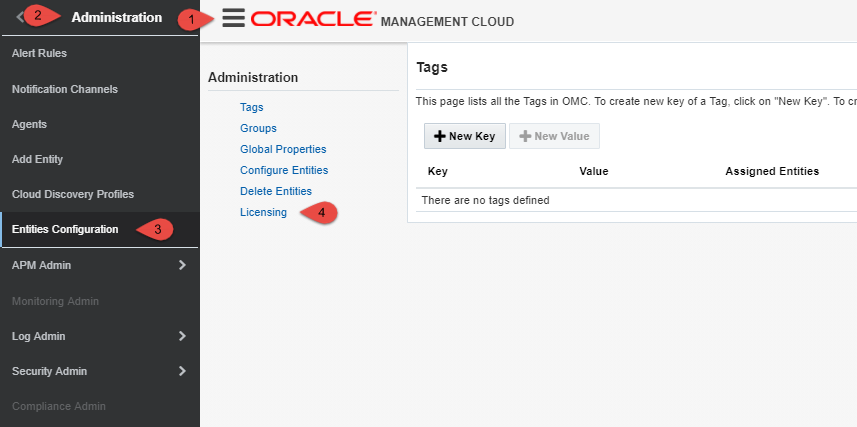
-
Click on “DISABLED” under “SMA Enrichment”
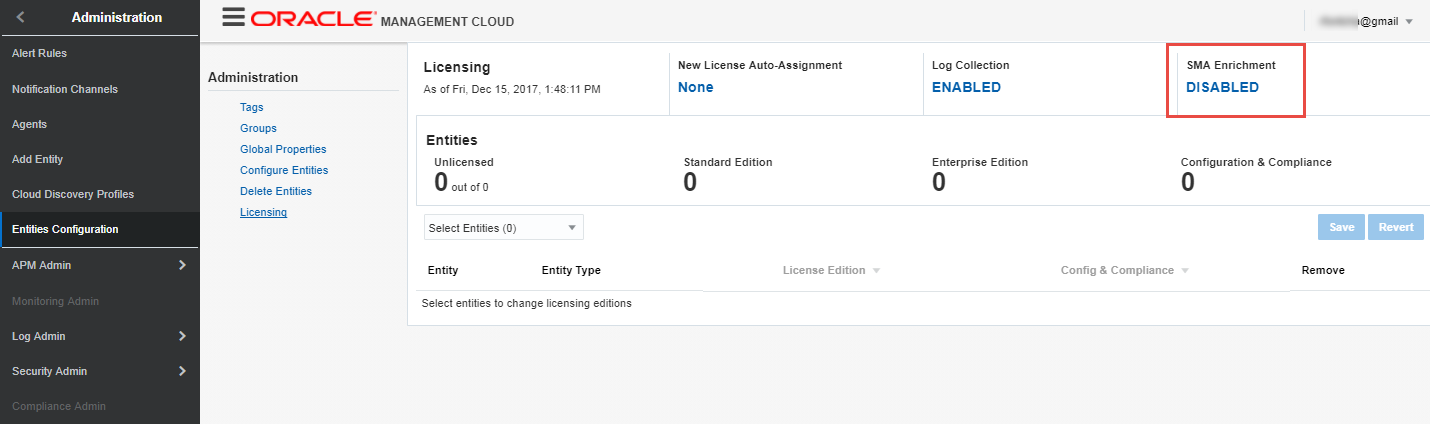
-
Push selector for “Enable Security Monitoring and Analytics” to the right and click “Apply” to enable
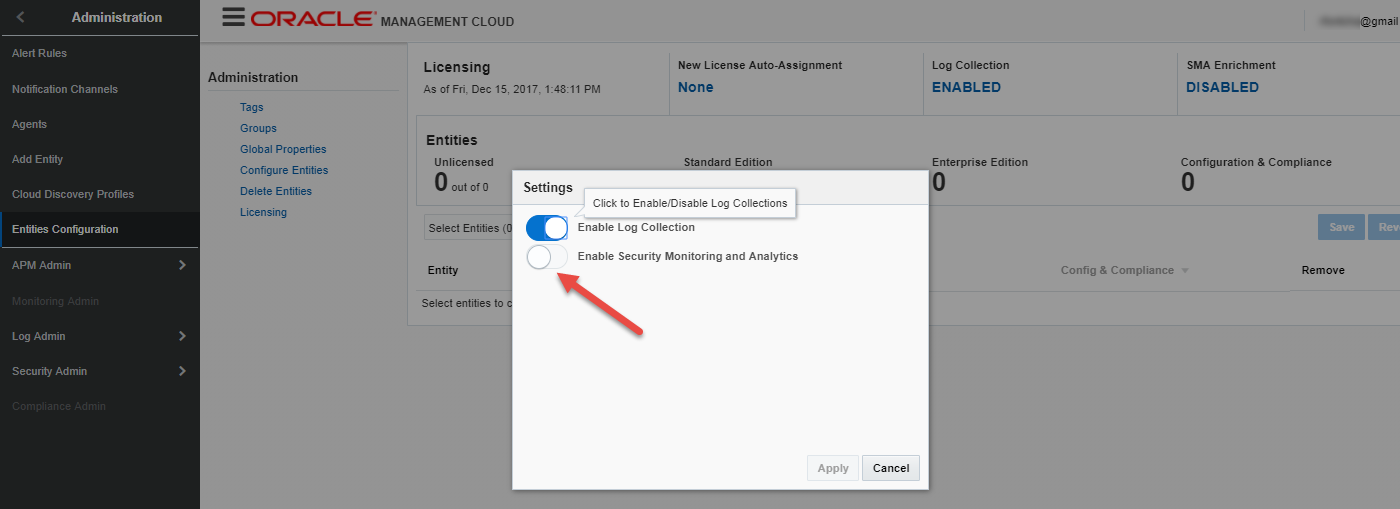
-
Enable New License Auto-Assignment by Clicking on “None”
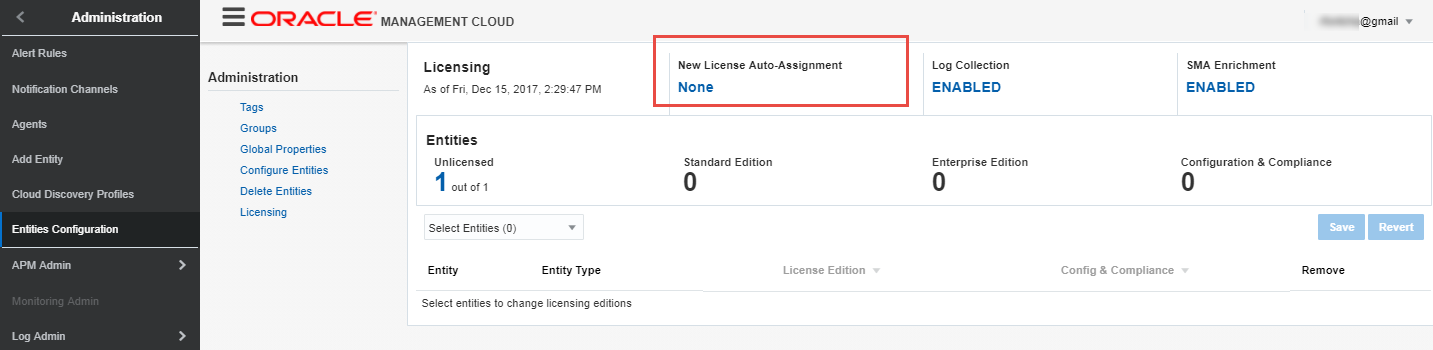
-
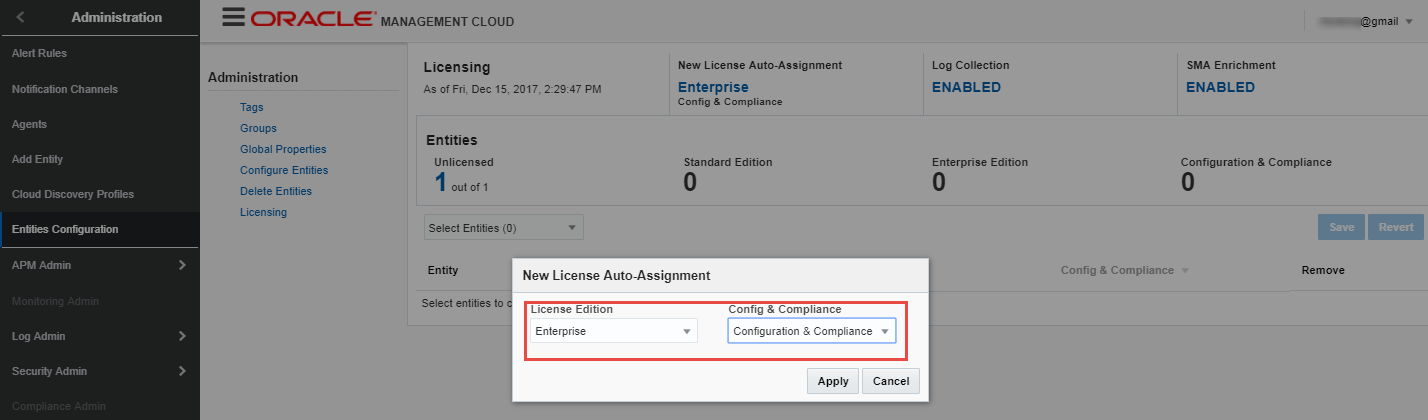
Toggle selector as shown below and click “Apply”
Create Security Monitoring & Analytics-based Alert(s)
-
Navigate
Menu Icon->Home->Administration->Alert Rulesand Select “Security Analytics” from the Drop-Down Menu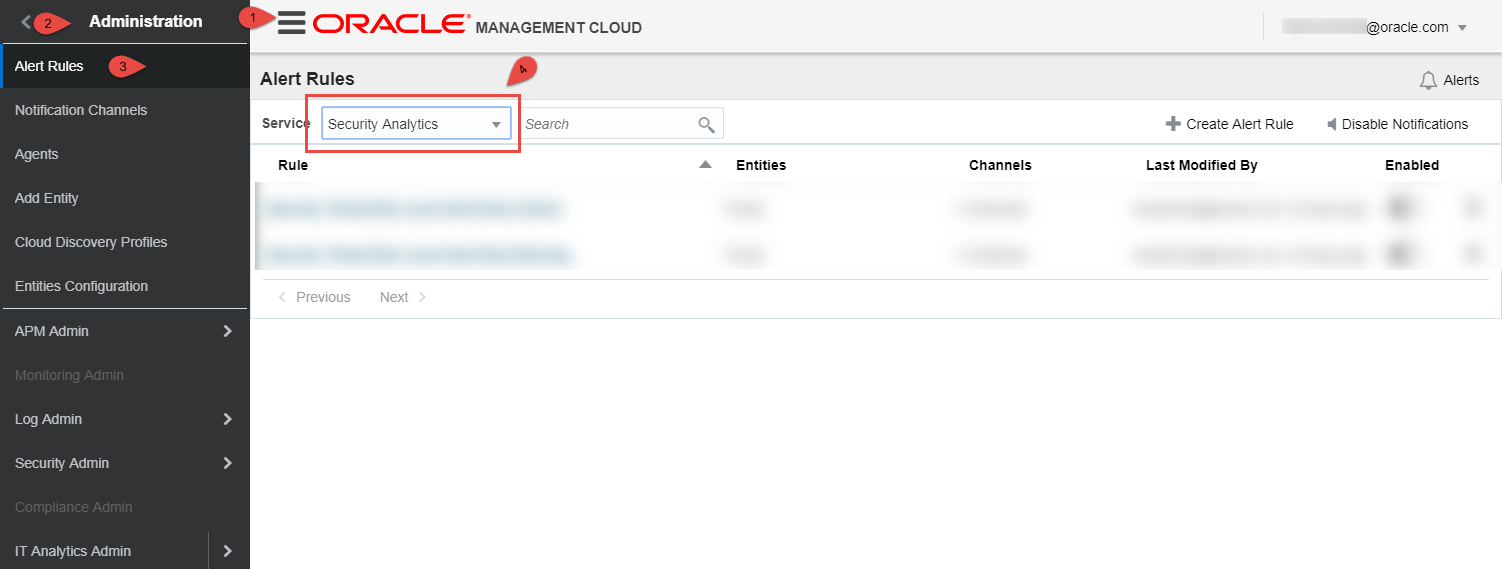
-
Click on “Create Alert Rule”
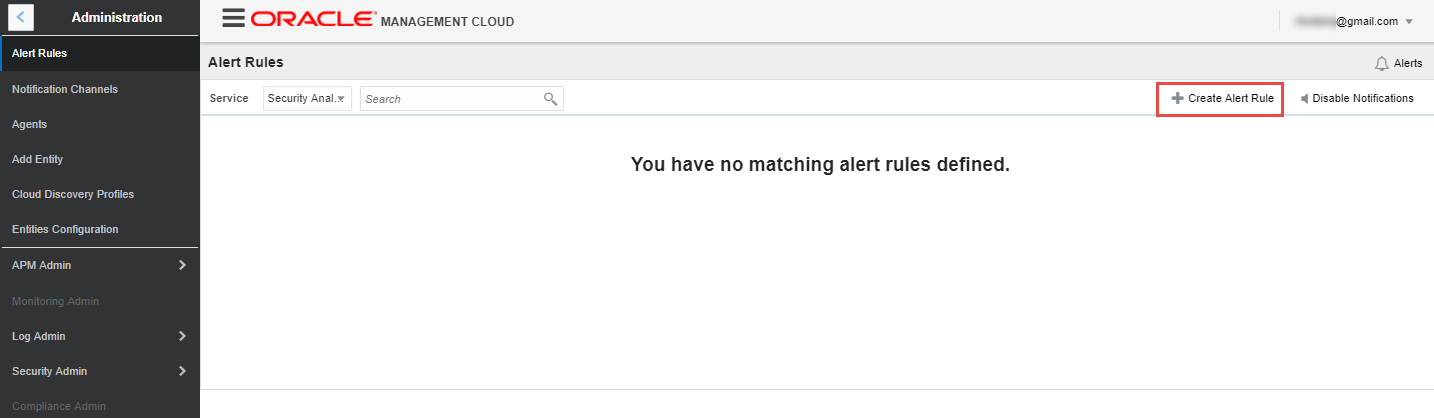
-
Follow the steps provided below to create the “Warning” alert rule. Fill in the form as shown below and click “+ Email Channel”
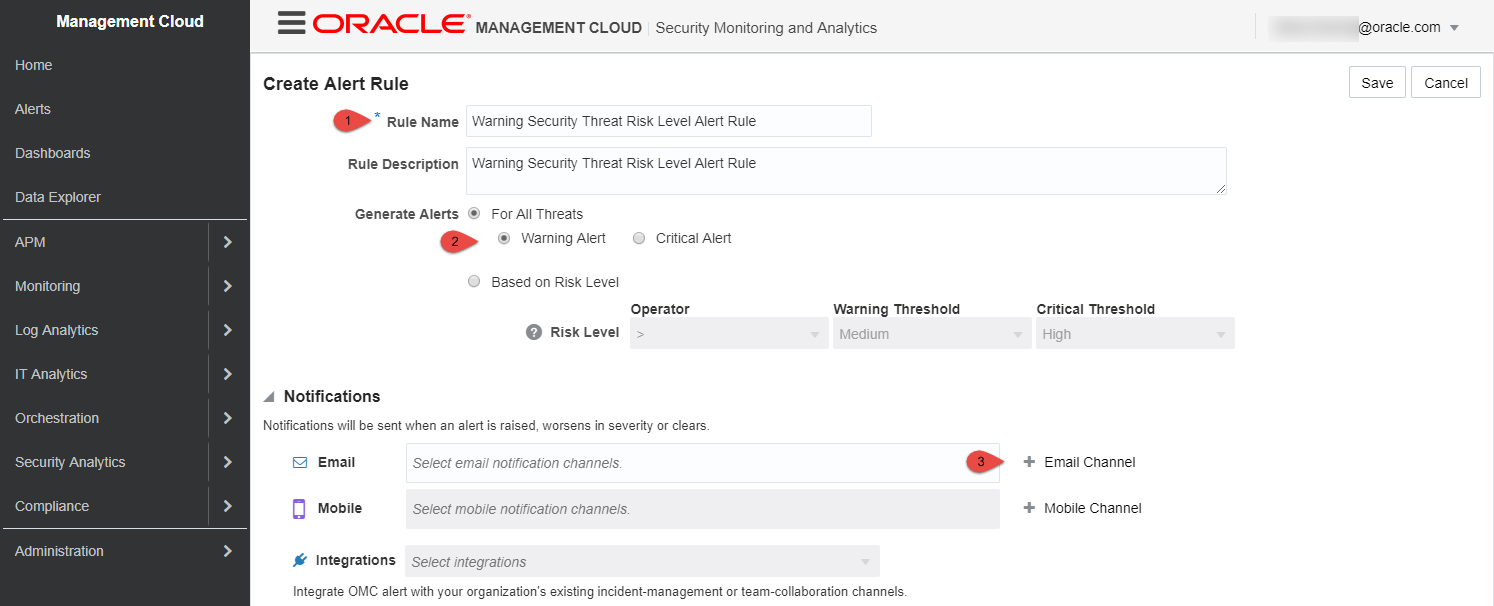
-
Fill in the form as shown below, click “Create” to add your first “Email Channel”, then click “Save” to create the “Warning” alert rule
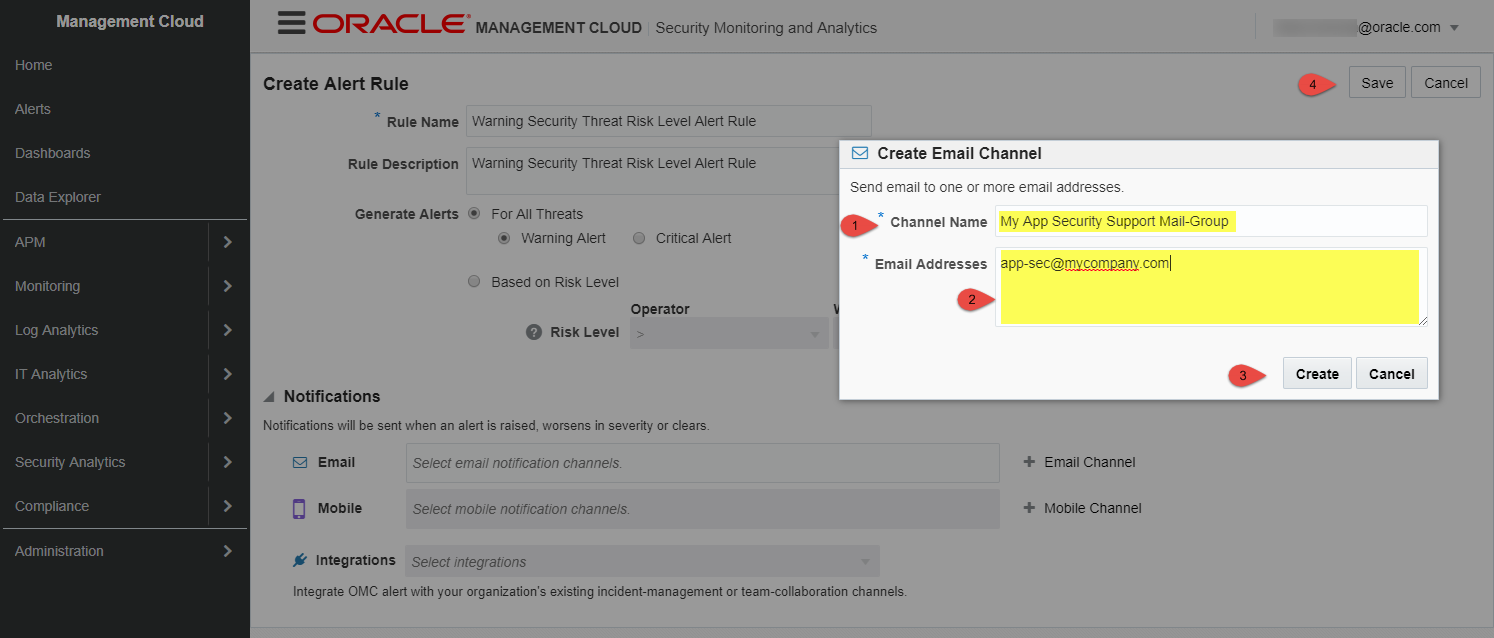
-
Optionally repeat step above and create the “critical” rule by switching from warning to critical
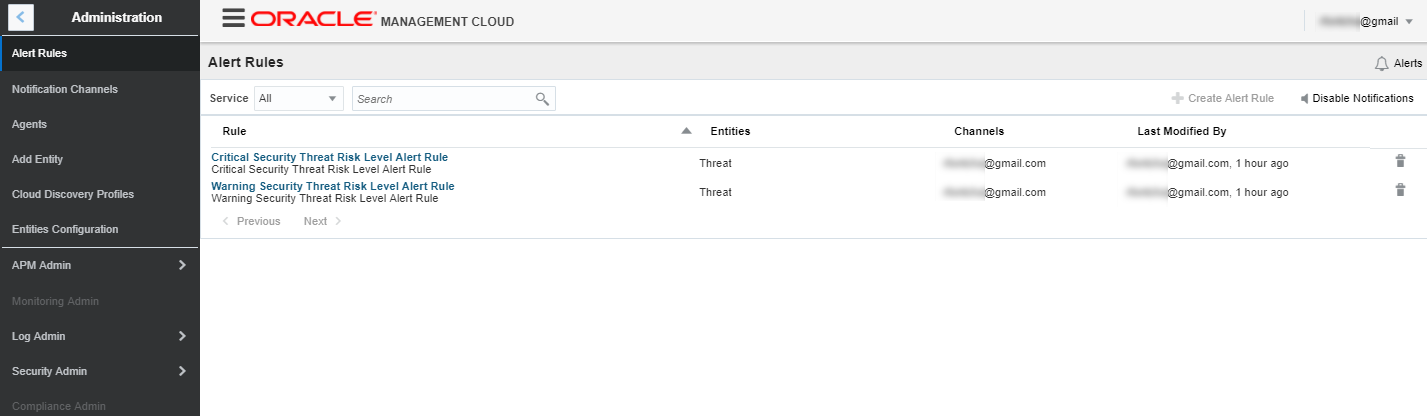
Review Correlation Rules for Evaluating Threats
-
Login to your OMC instance and select the SMA service
- Click the ‘Menu Icon’ to the left of Oracle logo in the top left of your window to access the menu
-
Click on Security Admin
-
Click on Correlation Rules
-
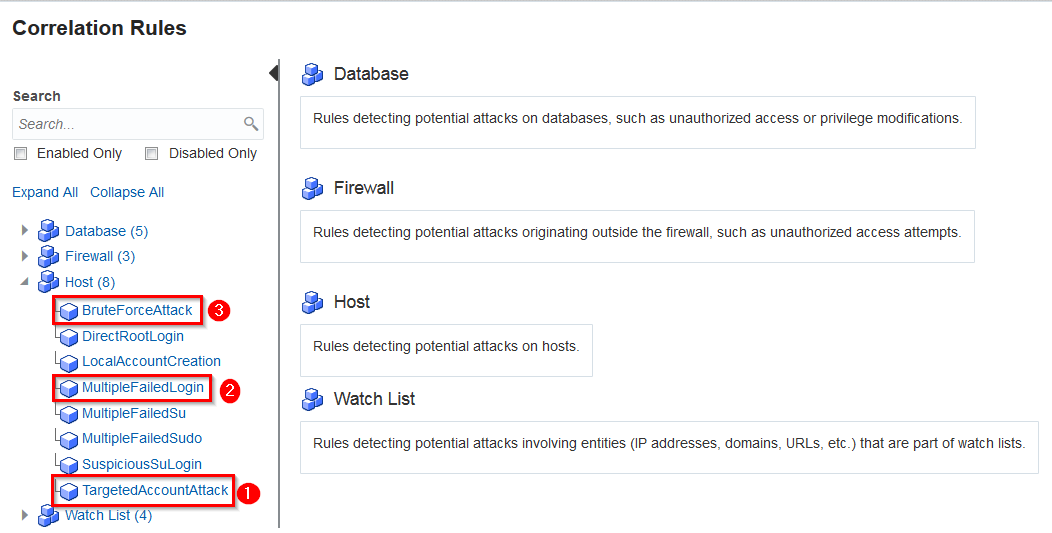
On the Correlation Rules screen, take a moment to explore some of the built-in correlation rules available within SMA for the purposes of threat detection. In today’s lab we will exercise three threats under the Host category
- Host
<-- Targeted Account Attack - Host
<-- Multiple Failed Logins - Host
<-- Brute Force Attack
- Host
-
Click on each one in turn and review the Definition as well as the Parameters available
- Access the sidebar menu again, and click on the back arrow in the sidebar menu, then select Log Explorer
-
Access the sidebar menu, select Log Admin -> Uploads
- For the moment, this page should be empty. In the next section, we will upload all relevant files and then return to this screen to review our uploads and check associated log data and then Activity in SMA
STEP 2 - On-Demand Security Logs Data Upload
There are multiple methods for getting data into your environment, the most common methods are installing Cloud Agents directly on the source machines in question or using the ODU method. For this lab, we will be using the ODU method.
Connecting to the Linux Host to Upload Test Data
On the shared Linux Server, you will find the sample data and upload scripts for the lab under /u02/stage. The host IP address and credentials will be provided by the instructor before the lab.
- Obtain the Linux server IP address and password from the instructor
- Using your preferred SSH utility from your laptop, login with OS username “cdsma”
Adding User Context to OMC
In addition to log data, sample user context data will be added to OMC as well to provide a richer experience by mapping users identified in security logs to detailed corporate directory sourced from the company’s Identity Service. In real production setting, this data will come from an Identity Service such as IDCS and by means of integration.
- In your SSH session, navigate to /u02/stage
-
From My Cloud Services Dashboard, toggle “Identity Domain” selector to your “Traditional” domain, then click on
Management Cloudas shown below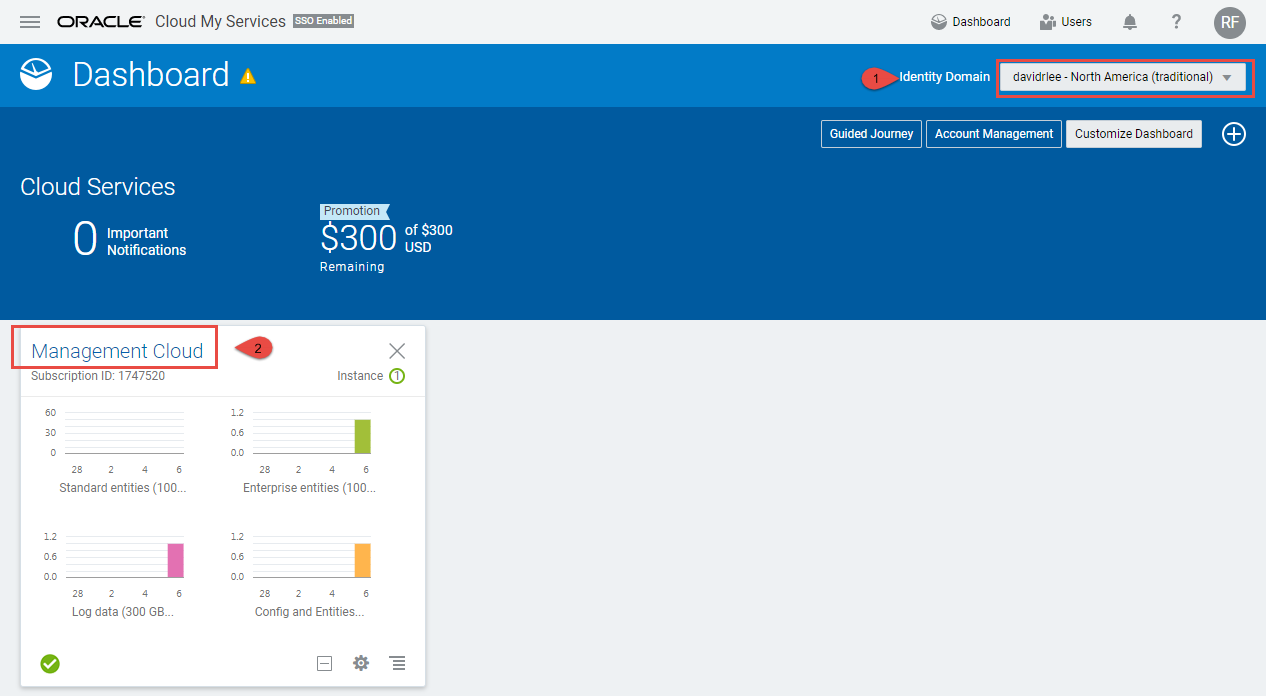
-
Get the Tenant ID, OMC Service Instance Name, and OMC Username as shown below
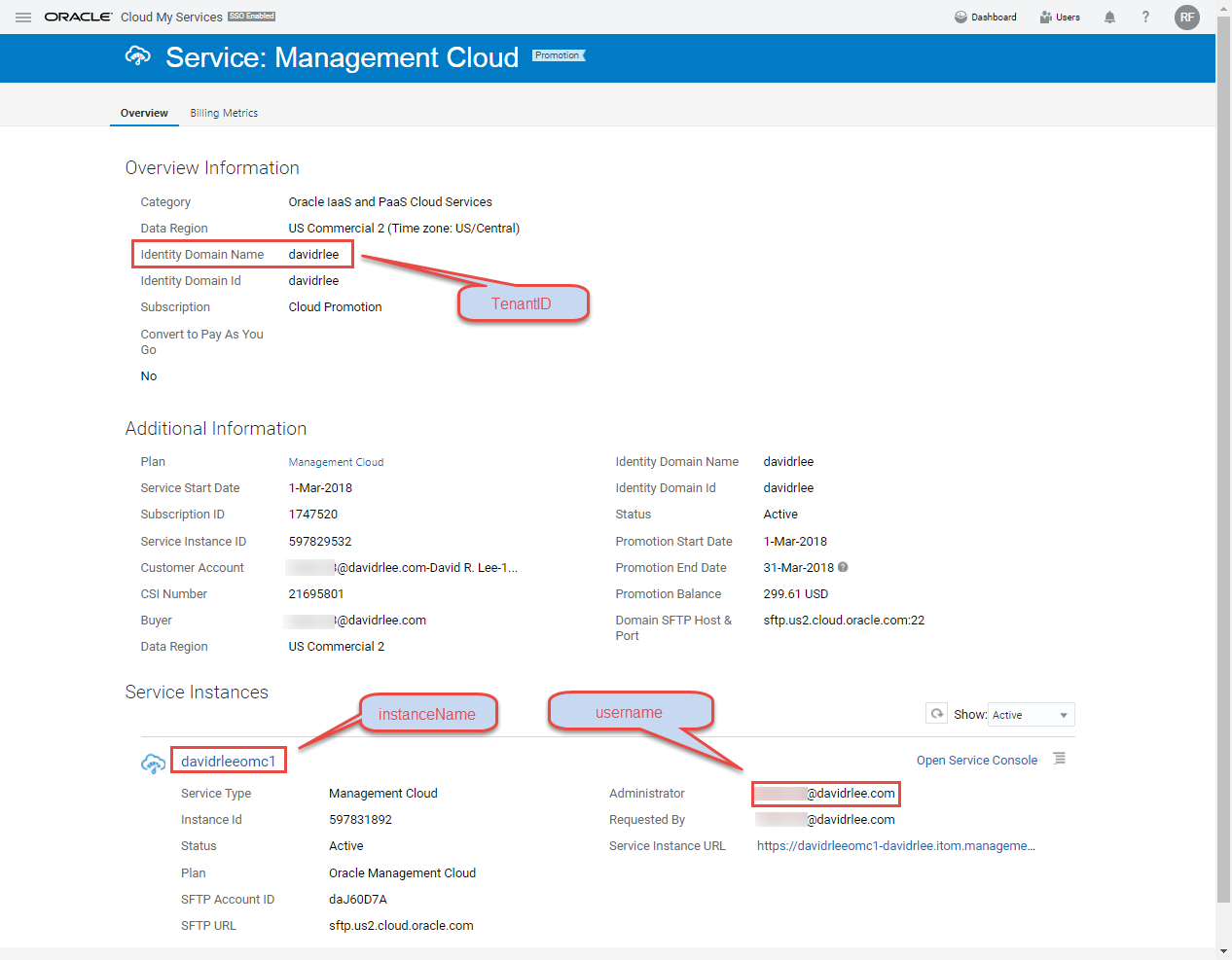
- Using the items gathered above, update environment variables accordingly as shown in this example
export tenantID=acmeinc #Tenant ID
export instanceName=ops #OMC Service Instance Name
export username=John.Doe@gmail.com #OMC Username
- Execute the Unix shell script
omc_upload_usr_context.shand type in your OMC account password when prompted to upload User context file
[cdsma@myhost]$ ./omc_upload_usr_context.sh
Uploading Linux Secure Logs to OMC
For the benefit of this lab, you will be uploading sample Linux Secure logs files to OMC covering the following 3 security threats types:
Target Account AttackMultiple Failed LoginBrute Force Attack
In real production setting, this data will be continuously streamed to OMC by OMC cloud agents and API integration. SMA supports uploading user data available in SCIM or LDIF format. The former will be used.
- From the same Linux host as indicated earlier and still with the environment variables set, run the Unix shell script
omc_upload_security_events.shto upload Linux secure logs.
[cdsma@myhost]$ ./omc_upload_security_events.sh
STEP 3 - Visualization - Review Log Data and Threat Activities
Once you have successfully uploaded the three log files, navigate back to the Uploads page. Refresh the page to see your uploaded log files.
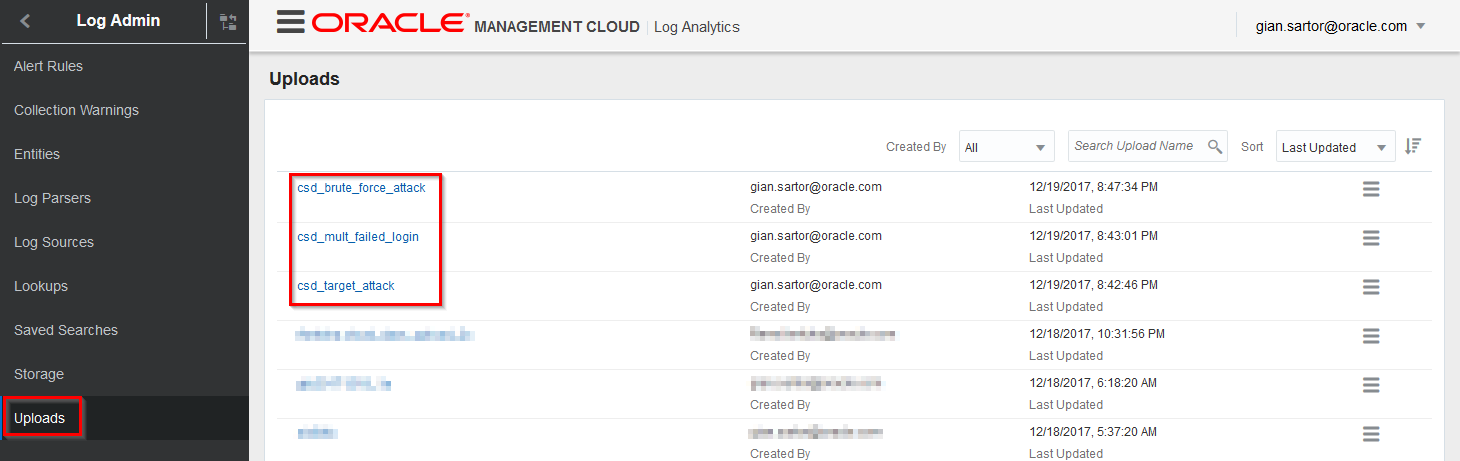
Review Log Data and Threat Activities in OMC
The data uploaded provides insights into key steps that make up what is known as a Kill Chain: Anomaly Detection ==> Reconnaissance ==> Infiltration ==> Lateral Movement.
Assess Linux Targeted Account Attack Data
You may recall that the definition of a Targeted Account Attack is 5 or more failed login events associated with the same user account are detected within an interval of 60 seconds across single or multiple endpoints from the Correlation Rules page we review earlier.
- Switch to your SSH session and open the linux_ta_attack.log file
[gsartor@lux sample-logs]$ less linux_ta_attack.log- Note the hostnames for
hr1andfinance1as well as the value forrhostanduser - Note how many records are in this file (12)
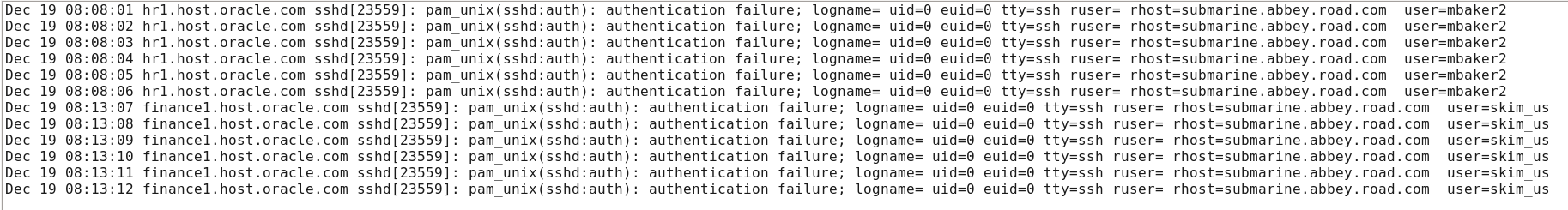
-
Switch back to your browser and to the Uploads page. Click the ‘Menu Icon’ in the csd_target_attack row and select View in Log Explorer
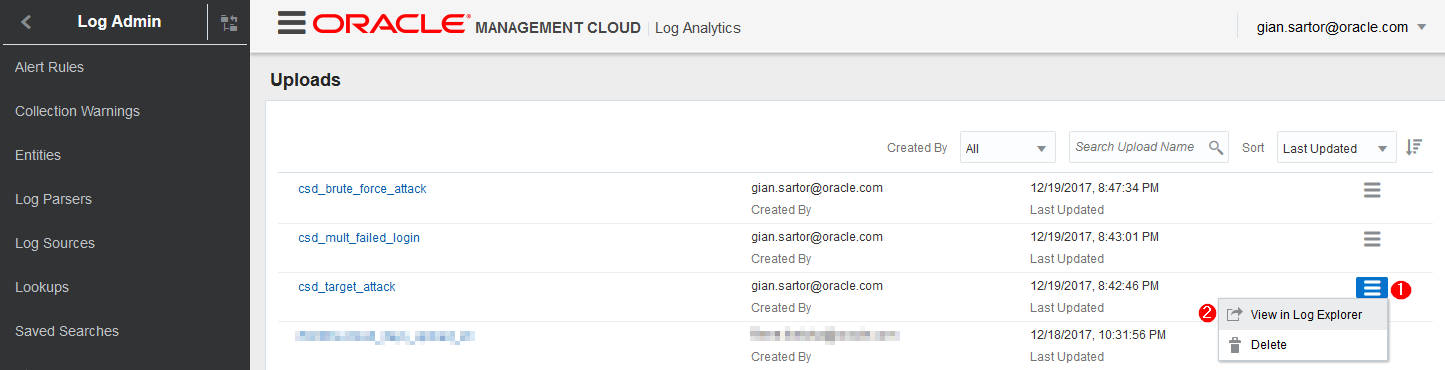
-
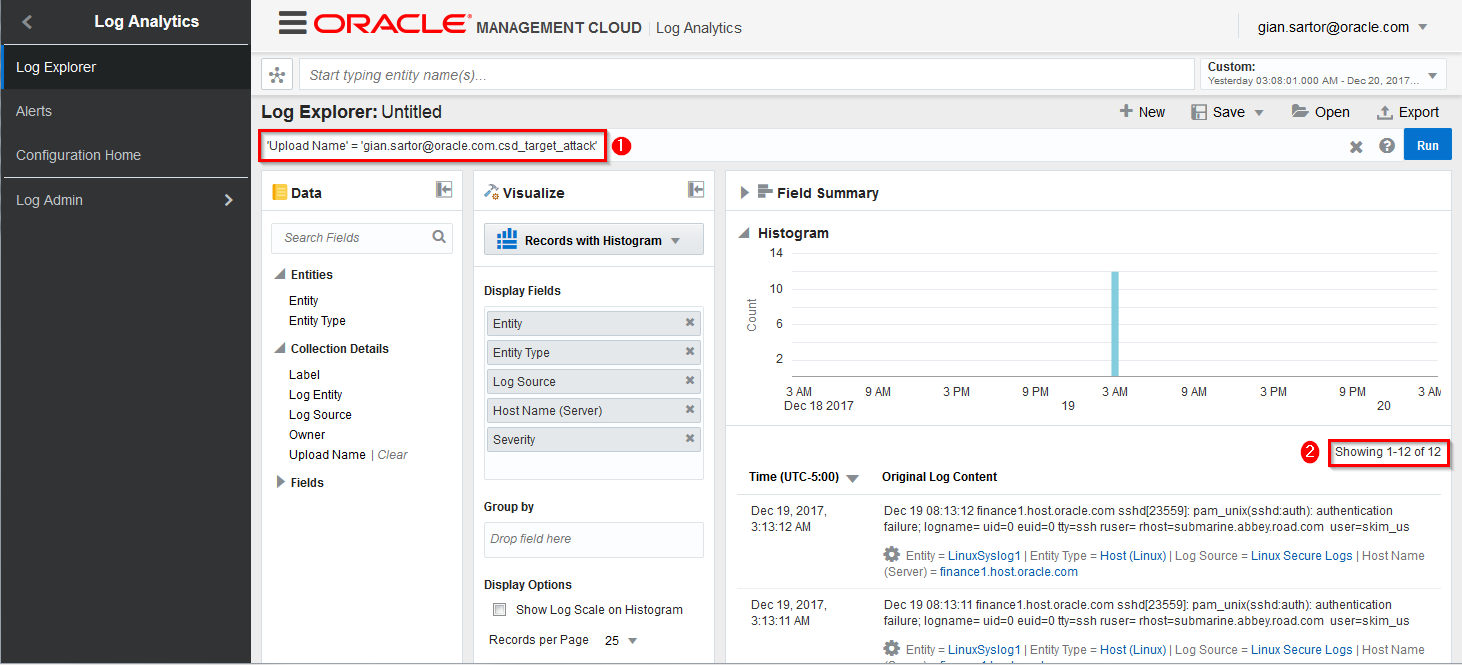
You are now viewing the log data in OMC Log Analytics. Security relevant data flowing to SMA goes through LA where it is enriched with security relevant tags. Note the filter being applied in the page as well as the number of relevant events (12).
- In the sidebar menu, click the back button in the top left-hand corner and select Security Analytics from the service list.
-
Toggle the timeframe selector in the upper righ-hand corner, set it to “12/18/2017 - 12/20/2017”, then return to the sidebar menu and click on
Activityto get a high-level overview of relevant security activities detected in your environment during that timeframe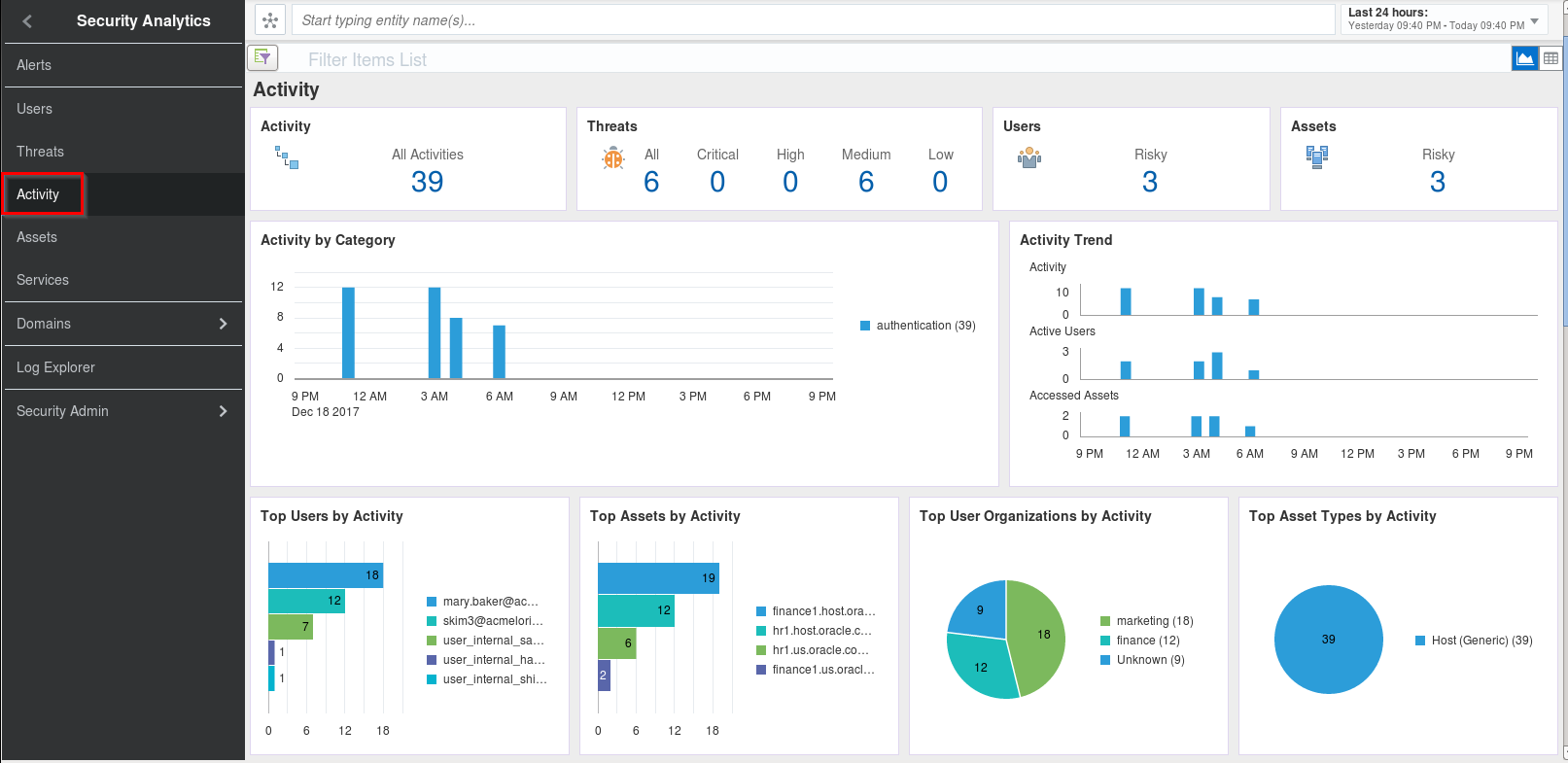
-
Scroll further down the same page to view a list of the activities
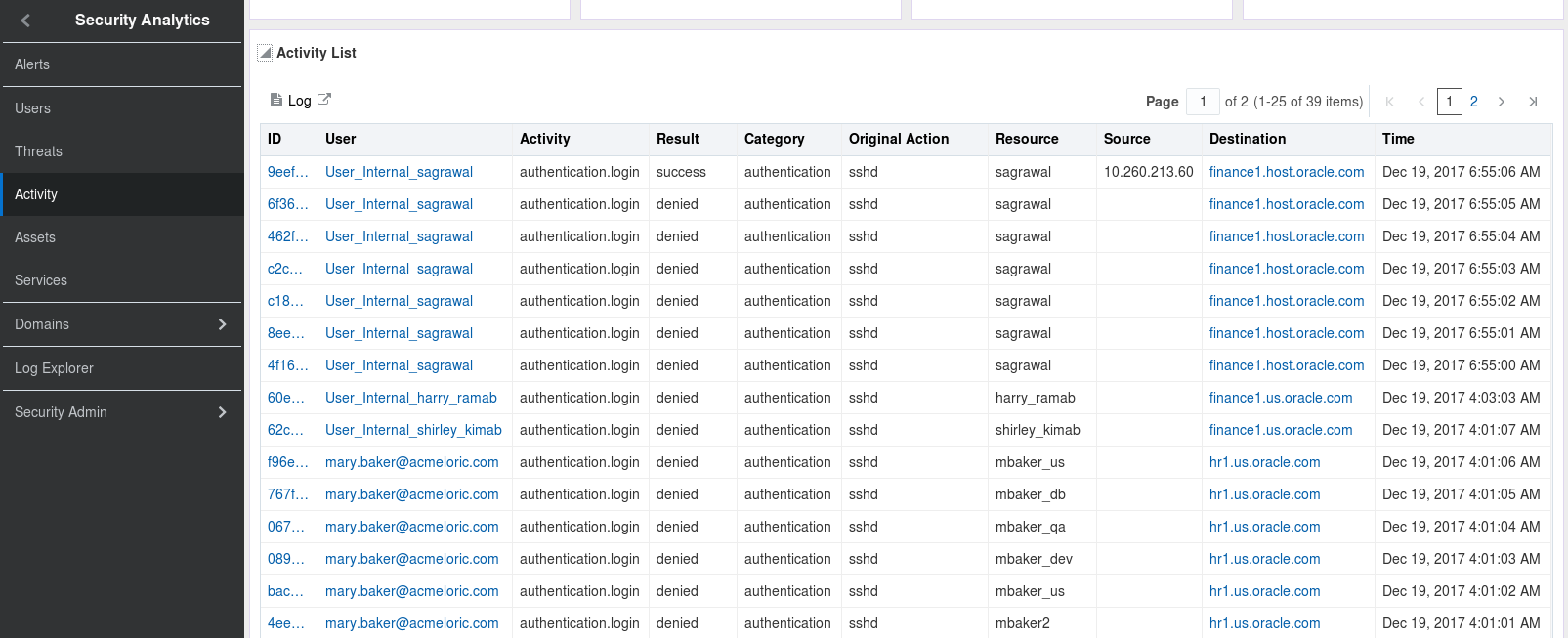
-
Click Threats in the sidebar menu, then click the number under All in the Threats section
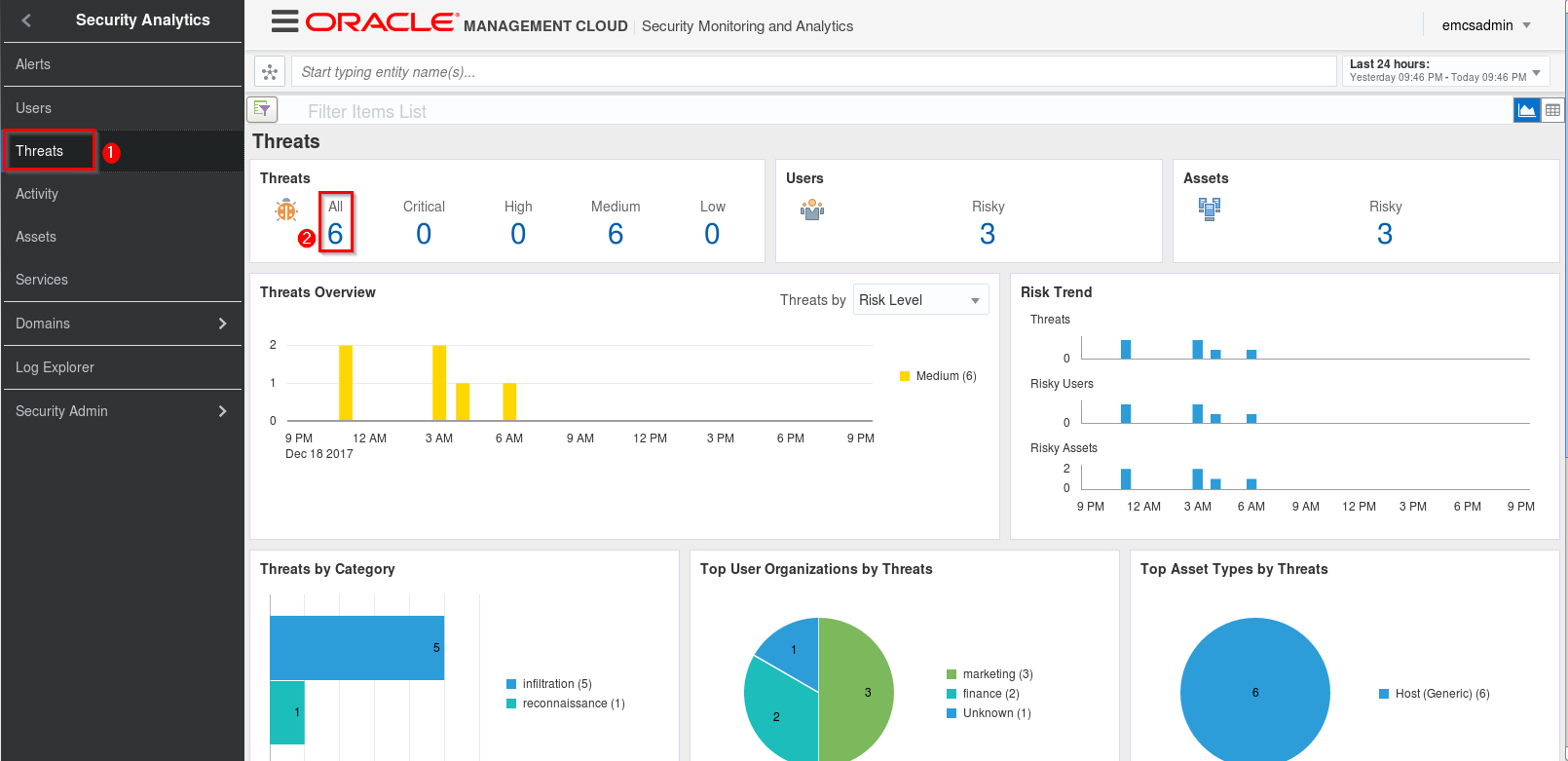
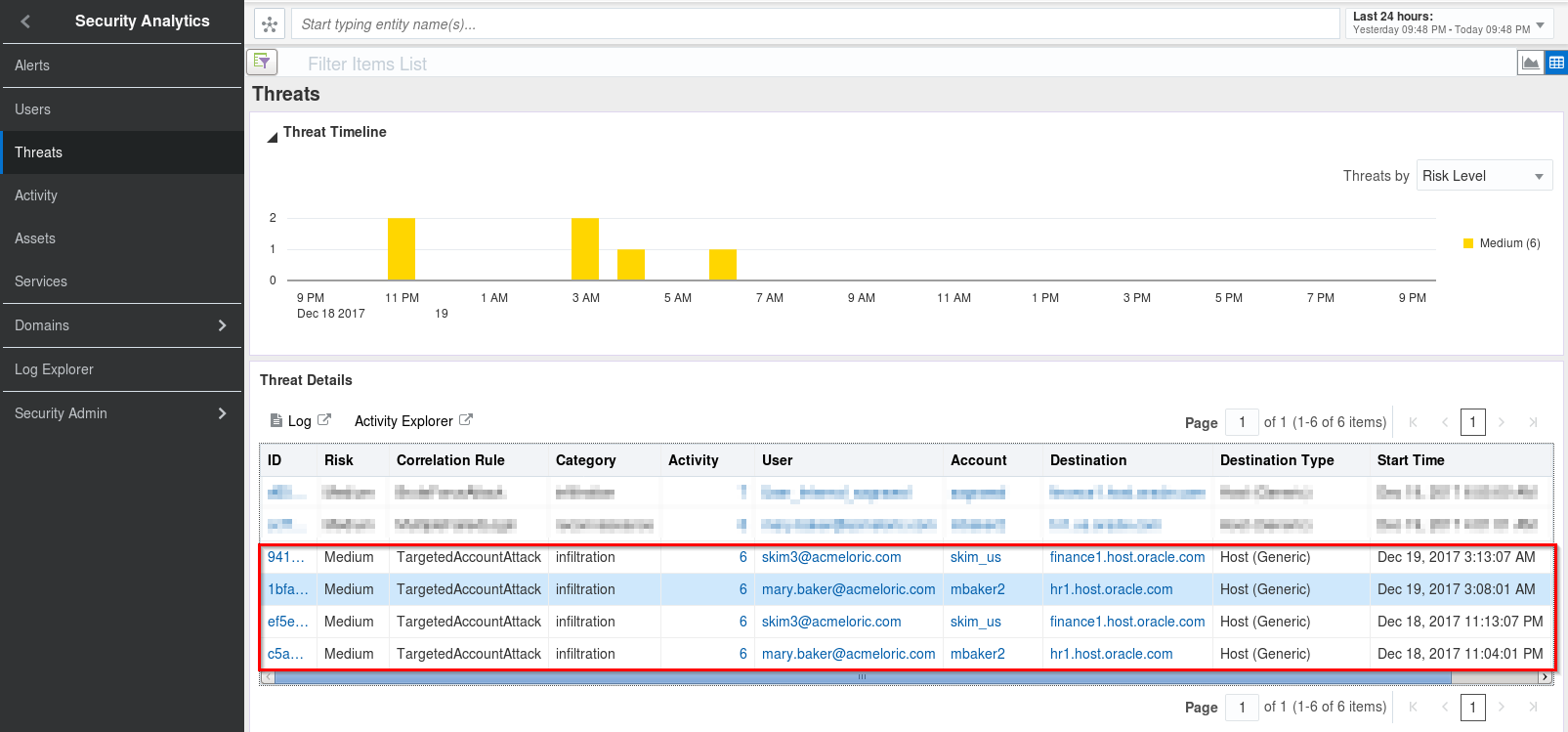
-
Scroll down to the bottom of the page and review the threat details. Note the Correlation Rule value as well as the Category type of ‘infiltration’ and the accounts being targeted.
- Now let’s repeat this process for the Multiple Failed Login and Brute Force Attack log files
Assess Multiple Failed Logins Data
Before reviewing the files, lets remind ourselves of the definition for Multiple Failed Login Correlation Rule, 5 or more failed login events are detected on multiple accounts on the same endpoint, within a time interval of 60 seconds
-
Switch to your SSH session and open the linux_mfl_attack.log file
[gsartor@lux sample-logs]$ less linux_mfl_attack.log- On this occasion, each failed login is for a different username. This is different from the Targeted User Attack we covered in the previous section.
- Note how many records are in this file (8)
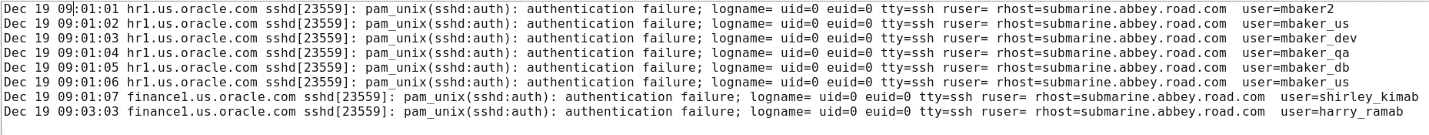
-
Switch back to your browser and to the Uploads page. Click the ‘Menu Icon’ in the csd_multi_failed_login row and select View in Log Explorer
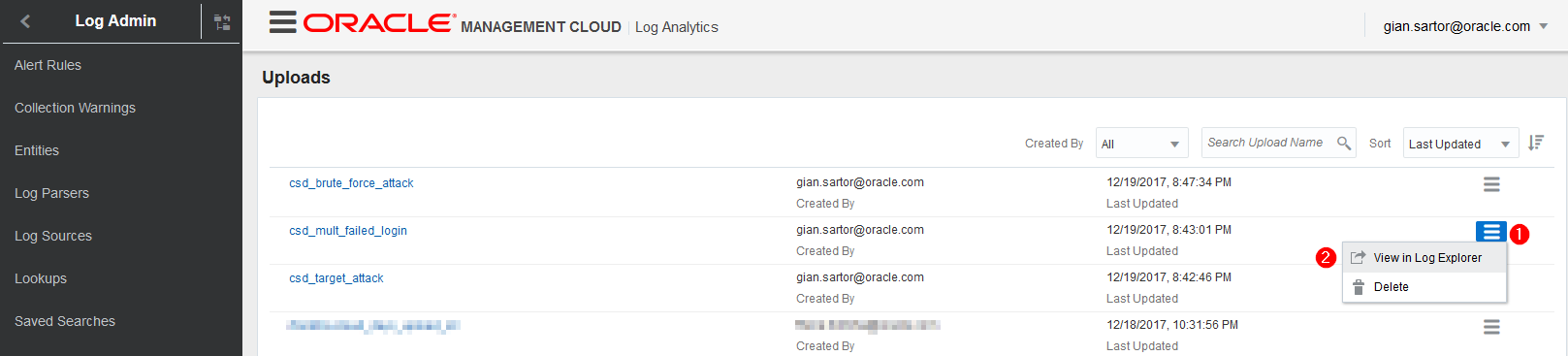
-
We are now back in Log Analytics and again take note of the filter being applied to the data we are viewing as well as the number of records being displayed. This matches the number of logs in our source file
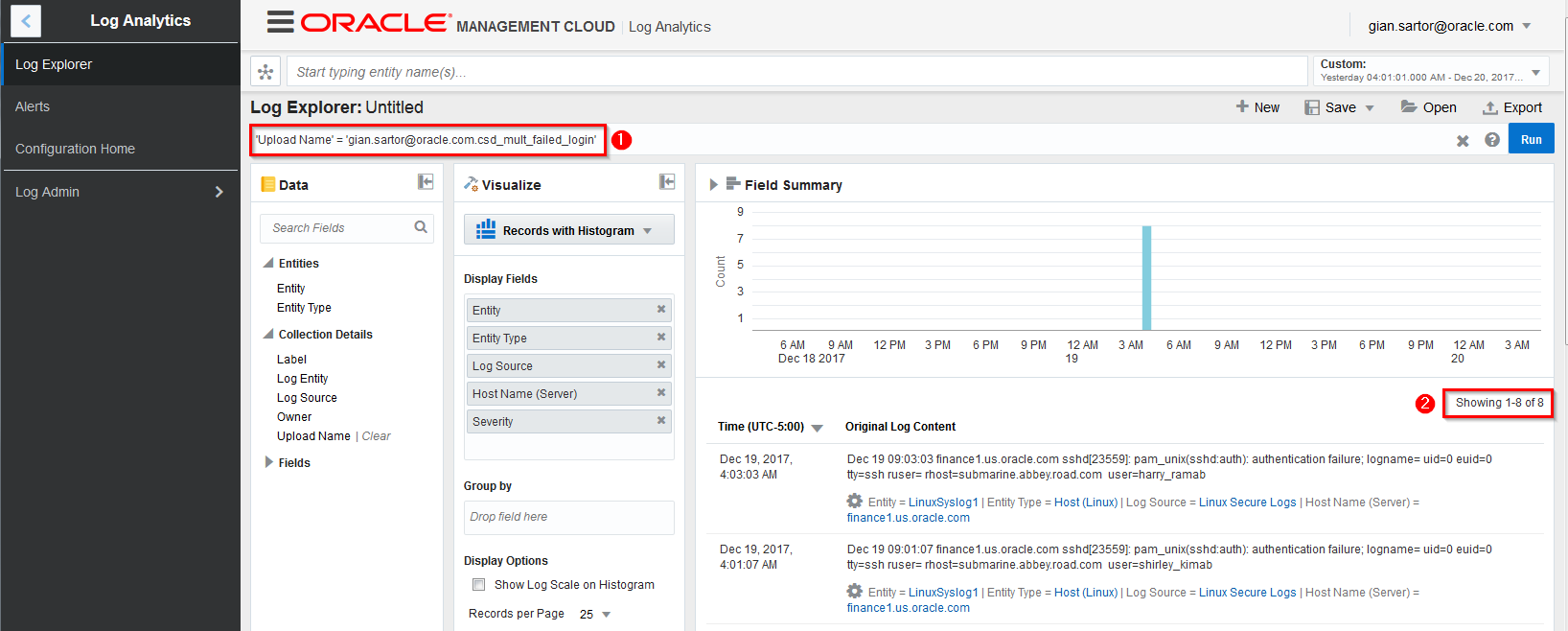
-
This time lets go straight to the Threats page in SMA. Once you are at the Threats page, click on the number below All in the Threats section.
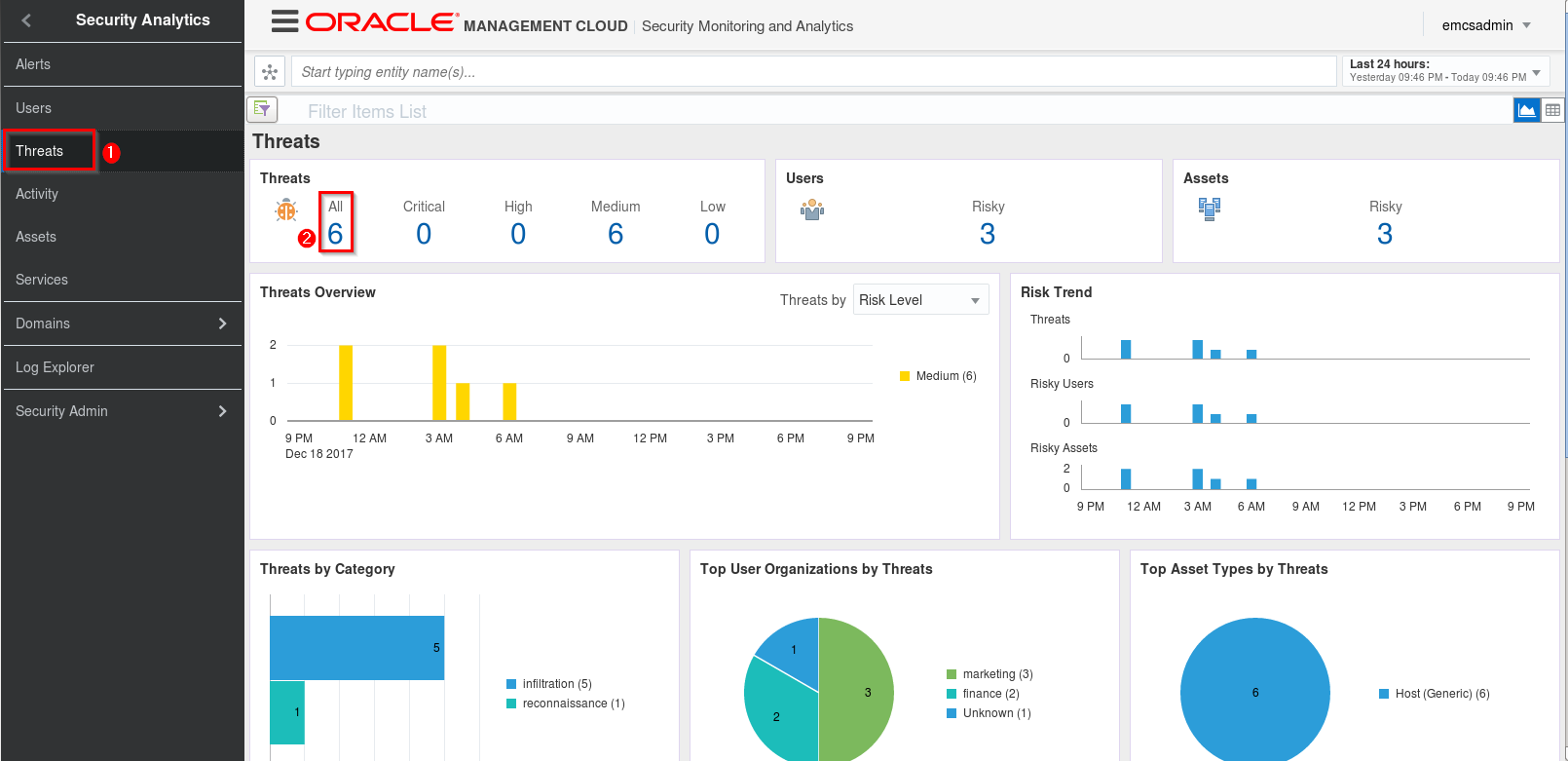
-
In the Threat Details section, locate the MultipleFailedLogin and click the ID
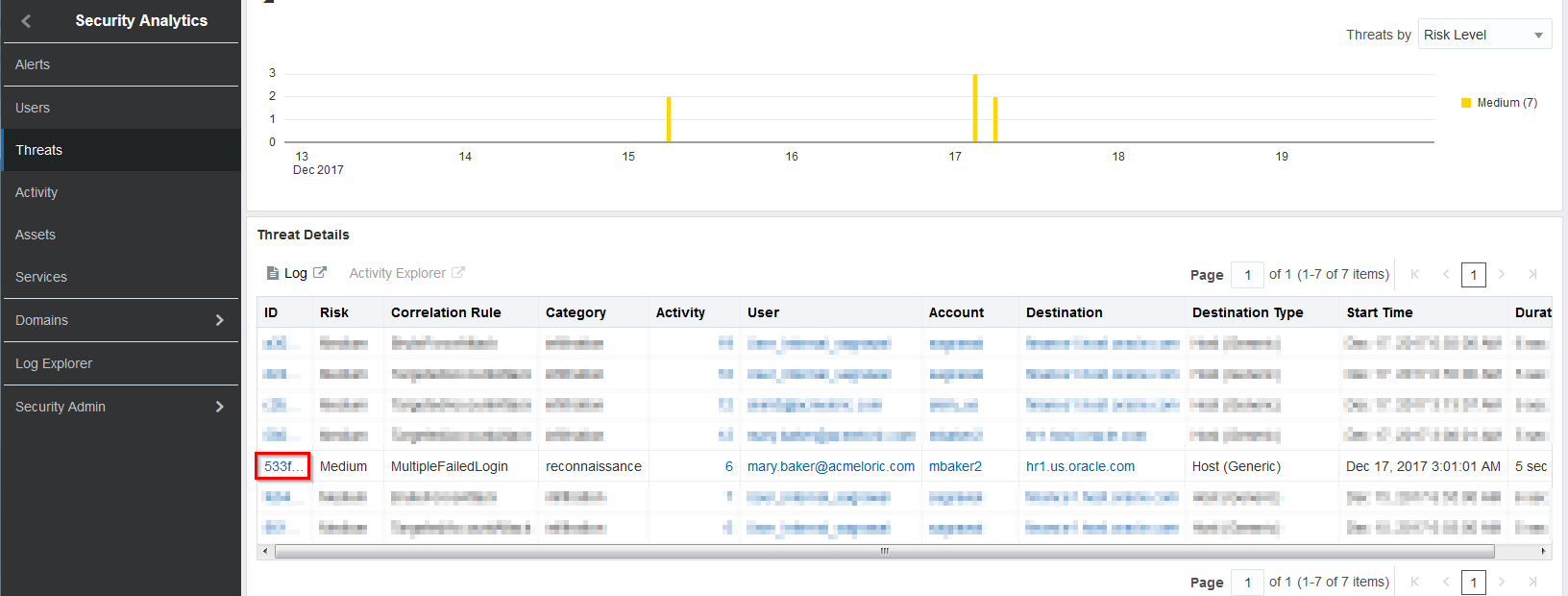
-
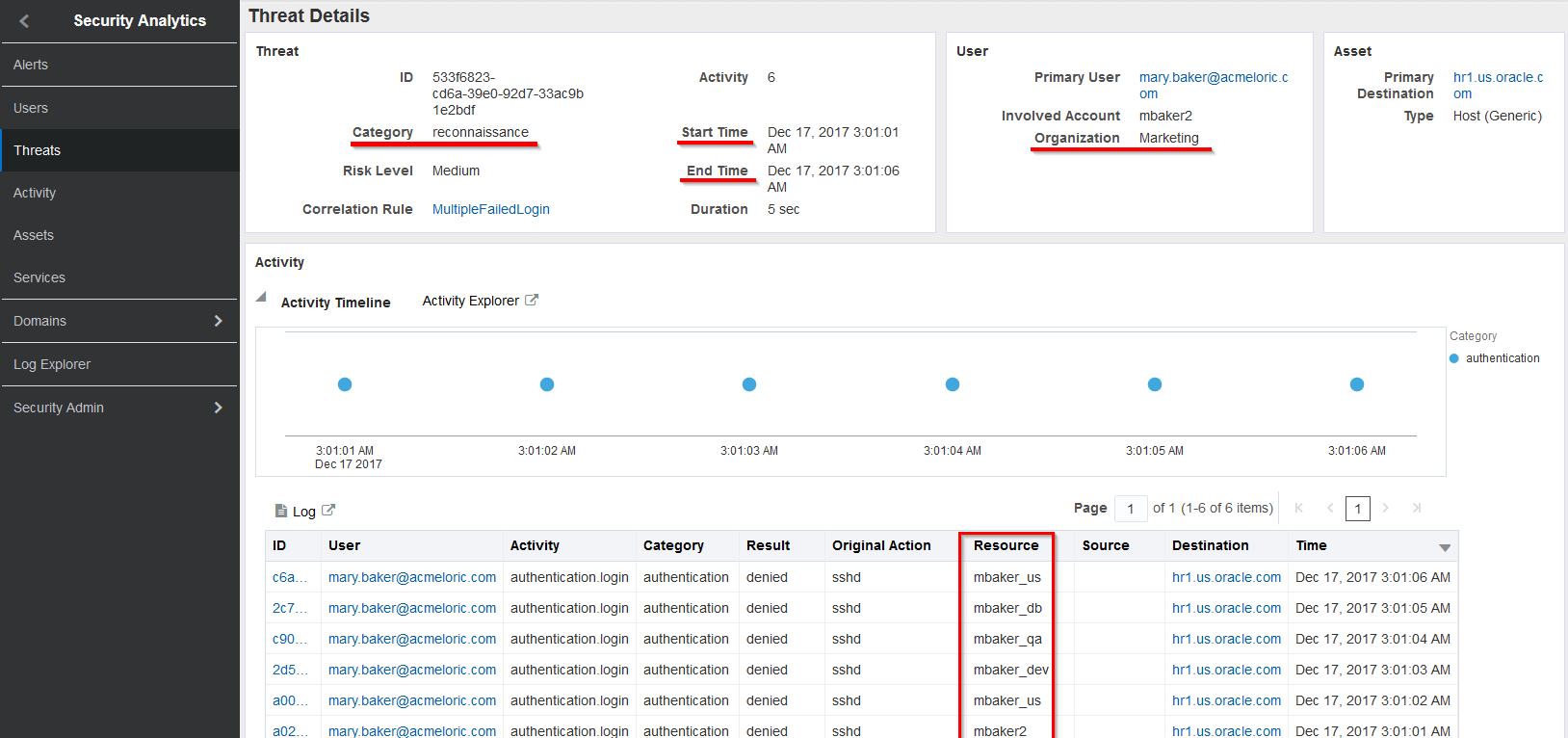
On the new Threat Details page, you now have access to a lot of detailed information for this specific threat. You can see the Category, Start and End time of this activity, the account being used for the attack as well as which Department that account belongs to, in this case Marketing. This departmental information came from our User Context Upload. Lastly, note the various usernames in the Resource column; the same as the ones in the upload file.
Assess Brute Force Attack Data
Finally, in this last section, we will assess the activity for a Brute Force Attack. Described as 5 or more failed login events are followed by a successful login on the same endpoint, associated with the same user account, within an interval of 60 seconds.
-
Let’s return for the last time the SSH session and review the upload file for the Brute Force Attack. Switch to your SSH session and open the linux_bfa_attack.log file
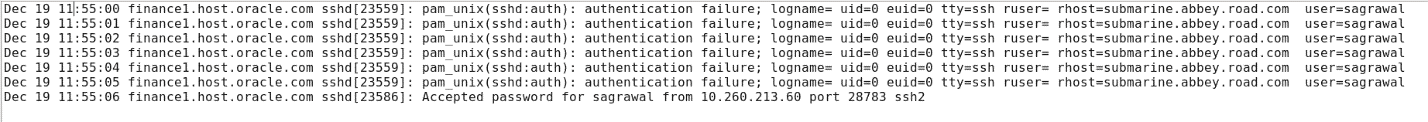
[gsartor@lux sample-logs]$ less linux_bfa_attack.log- Note the timing of the events, note that only one user is being targeted and lastly, note that we have a successful login on the last line
- Note how many records are in this file (7)
-
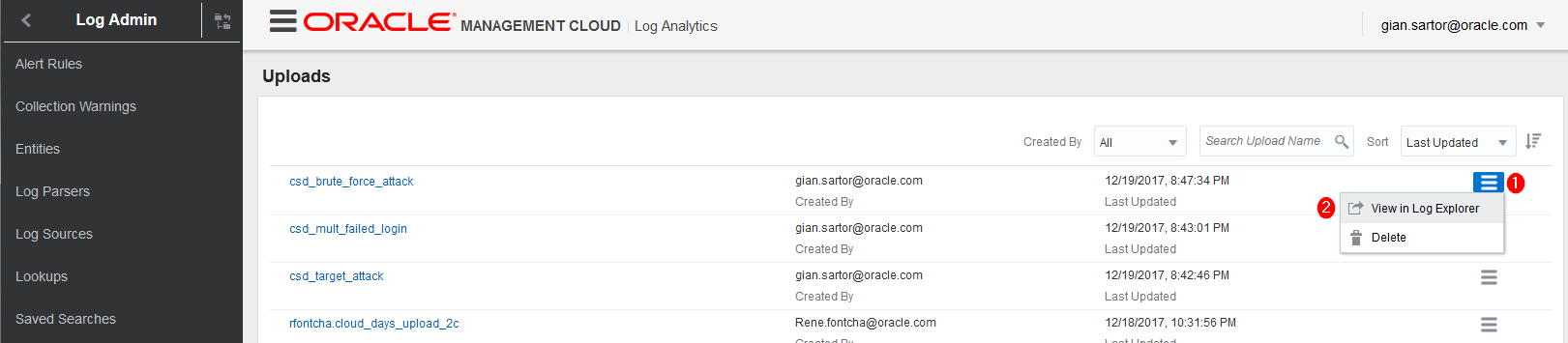
Switch back to your browser and to the Uploads page. Click the ‘Menu Icon’ in the csd_brute_force_attack row and select View in Log Explorer
-
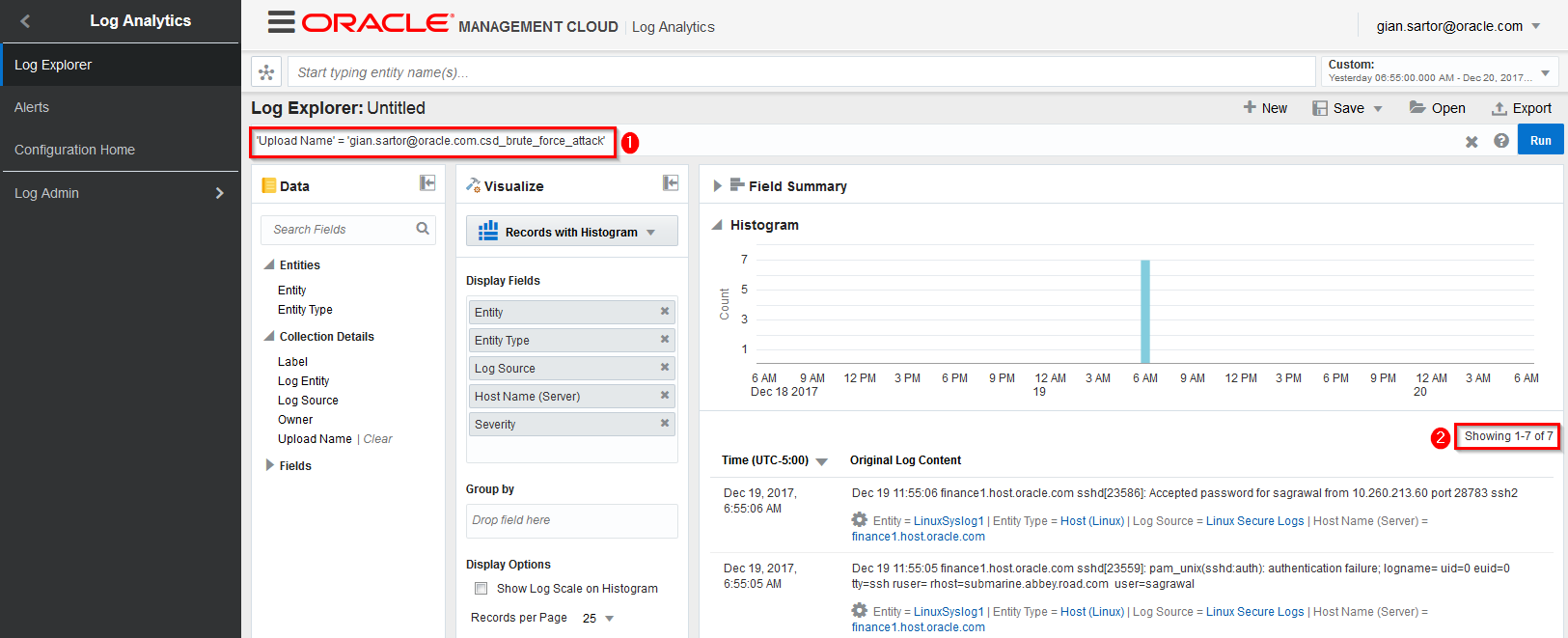
Back in Log Analytics and again take note of the filter being applied to the data we are viewing as well as the number of records being displayed. This matches the number of logs in our source file
-
Once again, we’ll go straight to the Threats page in SMA. Once you are at the Threats page, click on the number below All in the Threats section.
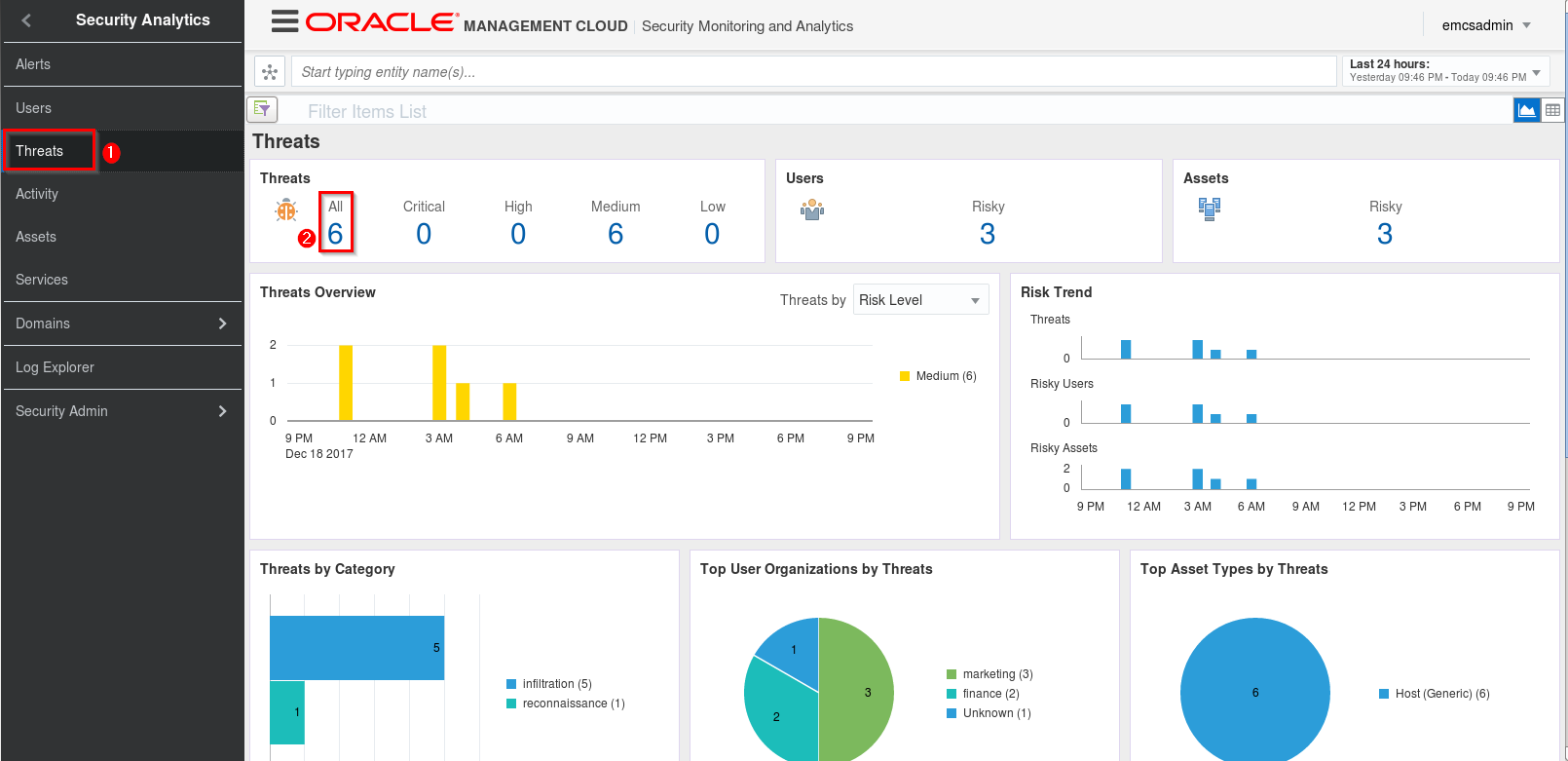
-
In the Threat Details section, locate the BruteForceAttack and click the ID
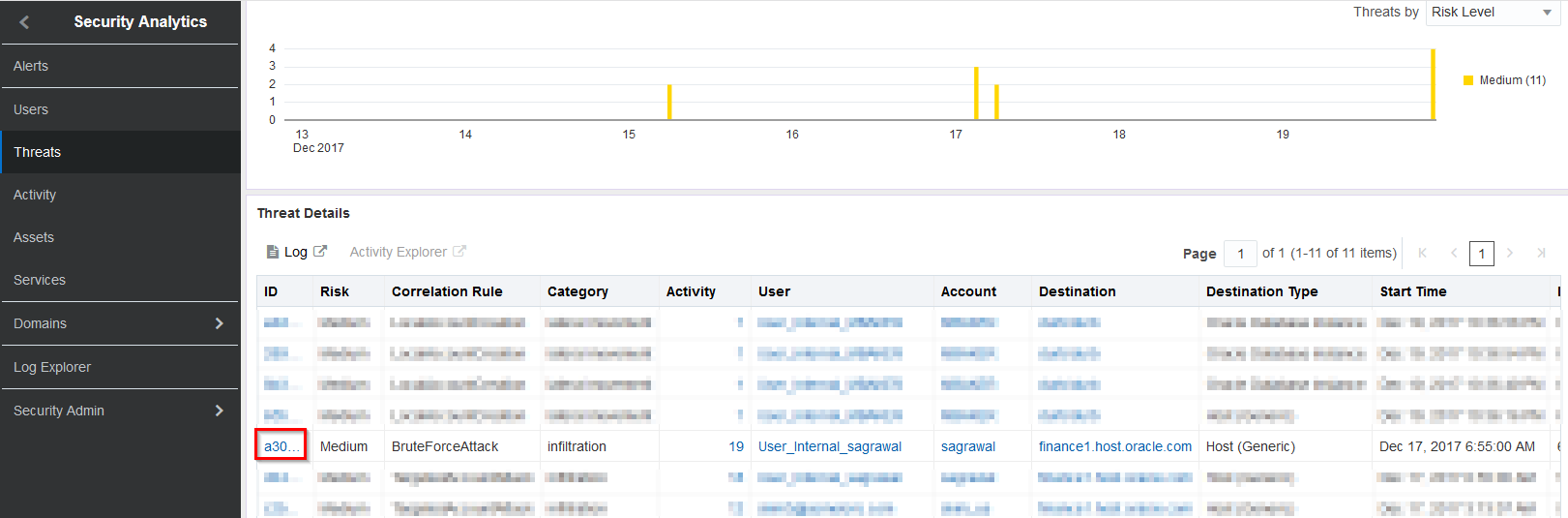
-
Take a few moments to review the details on the page, noting most importantly that we have many failed logins followed by a successful login.
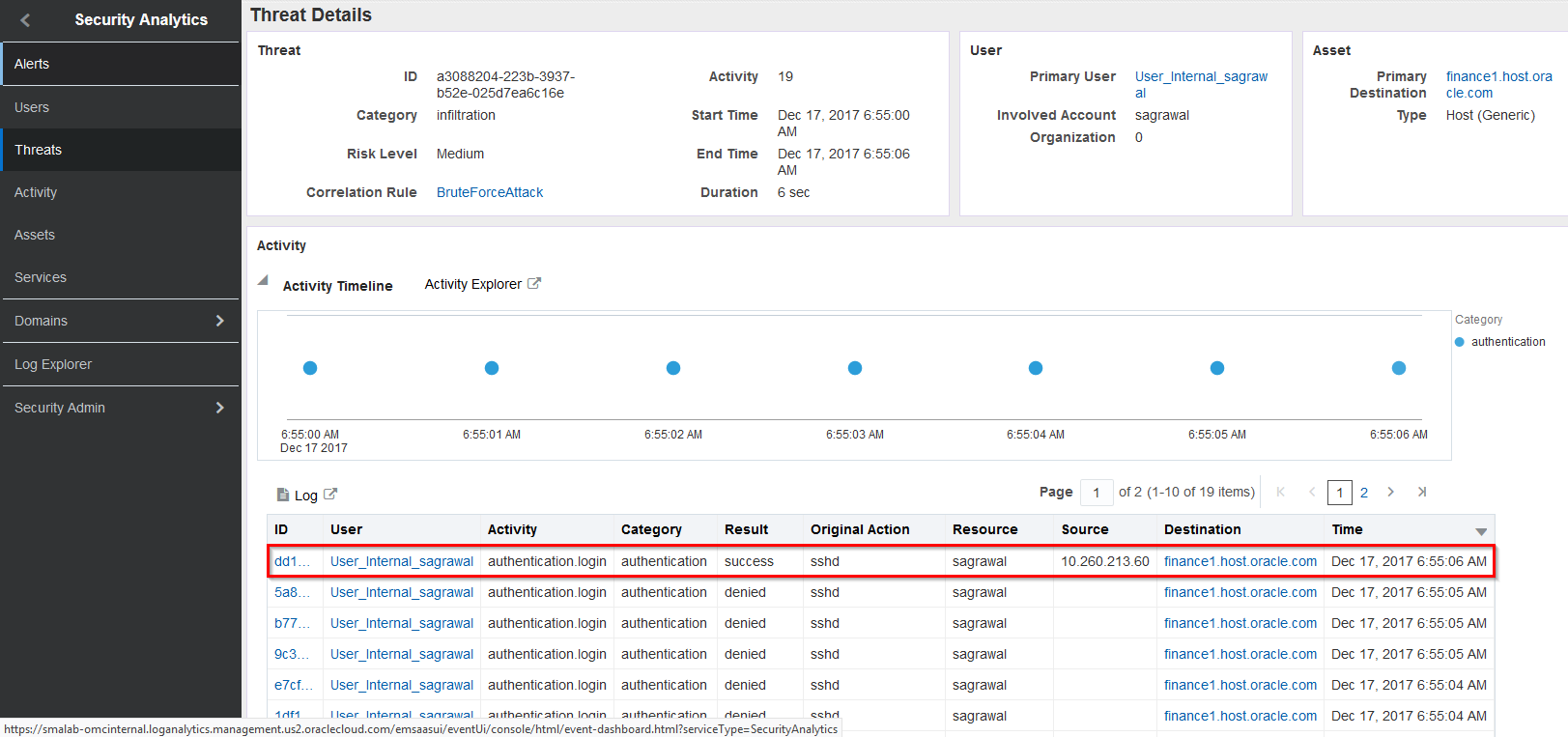
This concludes the threat assessment portion of this lab.
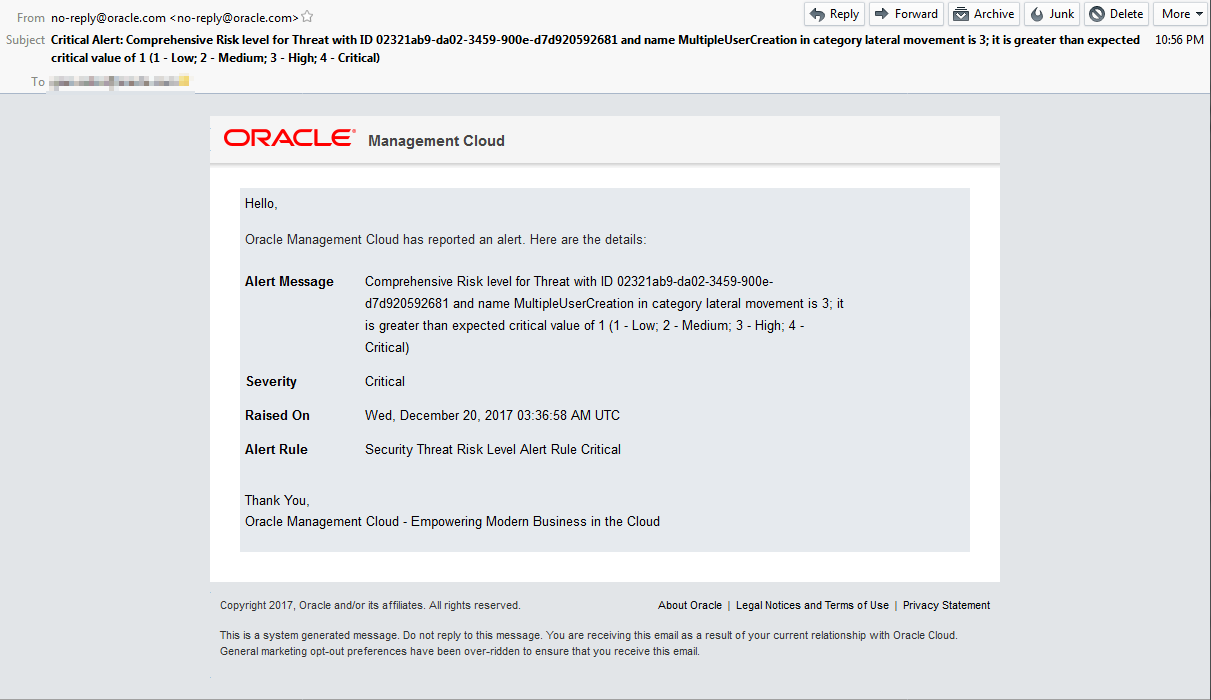
Review alert emails
In case you haven’t already noticed, you should have received some alert emails based on the activity we have been generating over the course of this lab.
Summary
In this lab, we:
- Setup alerts
- Reviewed Correlation Rules in SMA
- Uploaded data to your environment
- Assessed the threats associated with the data uploads
- Navigated through the user interface of both the Log Analytics Cloud Service as well as the Security Monitoring & Analytics Cloud Service
- We saw how SMA categorizes threats and how we can enrich the log data with user context
- Understood what comprises a kill chain and why that is important
- Reviewed alert emails